
Free plan
A security stack so powerful you won’t believe it’s free.
Discover vulnerabilities within your system in a glimpse. Enhance your daily operations and prepare for pentesting.
Products
All-in-one solution
Detecting every possible thread, from simple bugs to cloud misconfigurations and malicious URLs.
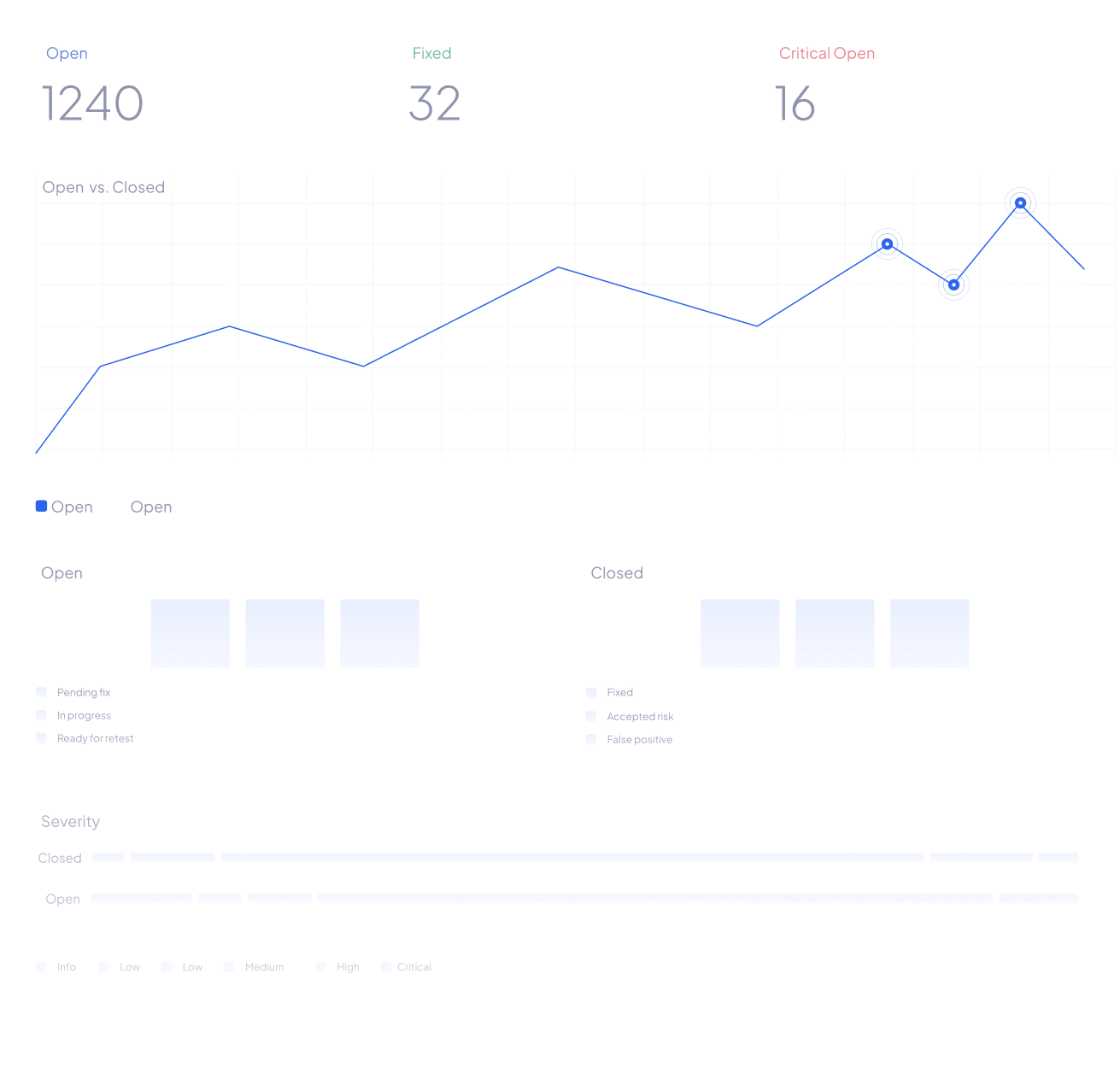
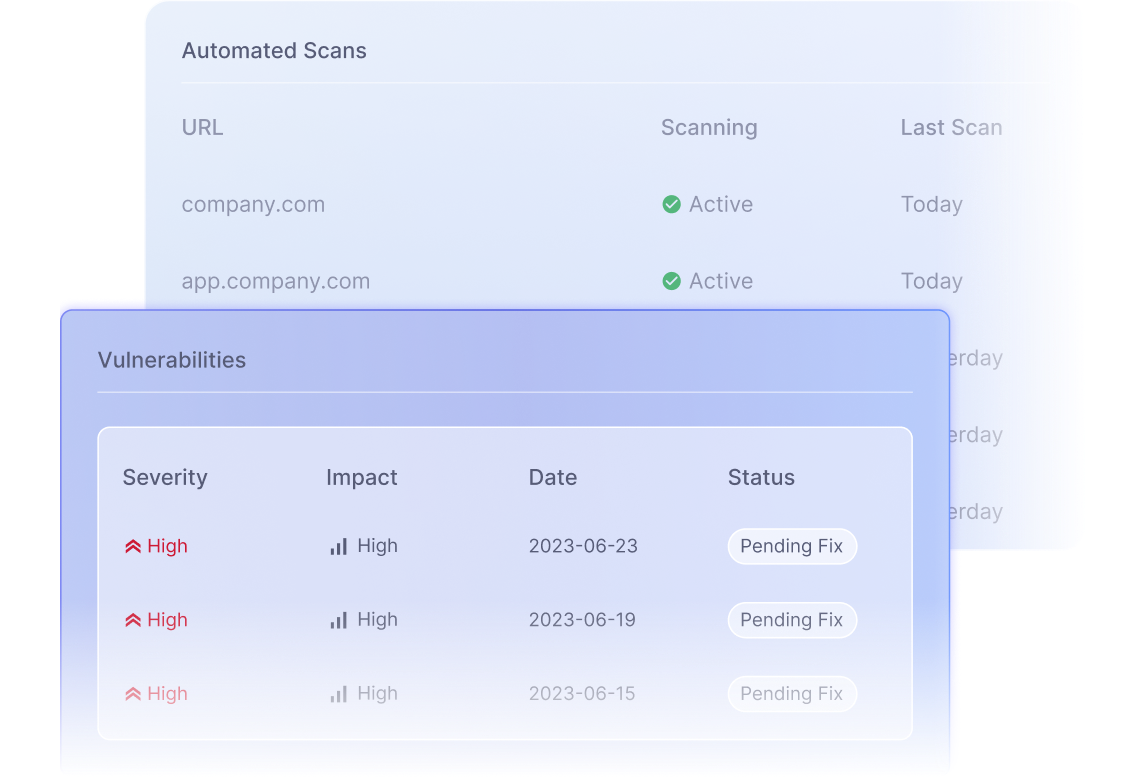
Automated Scans
Get your web-apps continuously scanned to find security vulnerabilities in development, staging and production environments. Strengthen your overall security over time.

Speed and efficiency
Select the URLs you want to test and start the scanning immediately. Get your results in minutes.
Recurrent scanning
Scan your apps continuously to improve the cybersecurity standards of your company.
Multi-target testing
Instead of testing one URL at a time, use parallel scanning to discover the vulnerabilities of every one.
Attack Surface Monitoring
Maintain a continuous discovery and inventory of your organization’s assets. Prioritize your cybersecurity operations backed by data.
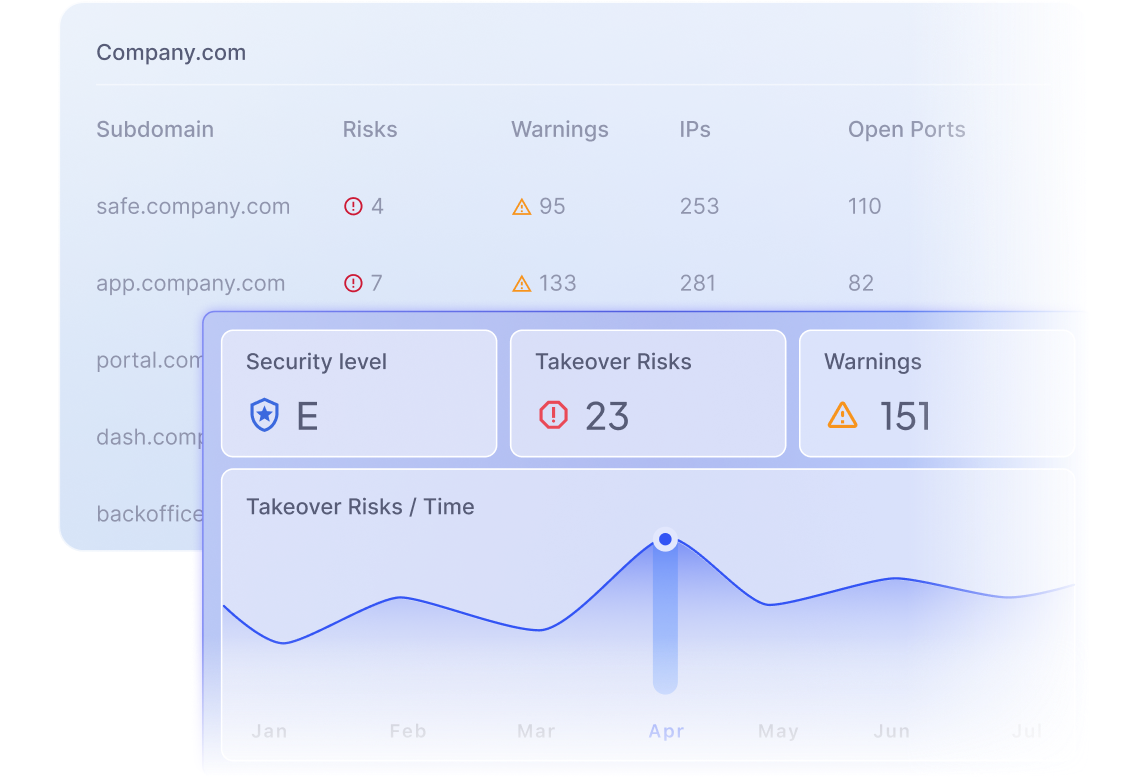

Discover takeover risks
Examine, analyze, and assess your cybersecurity in your cloud infrastructure. Identify all of your potential threats and obtain actionables, all in one place.
Find open ports
Get warnings about open ports on your network. Address each alert to reduce the likelihood of any issue.
Scan DNS infrastructure
Scan all DNS servers within your infrastructure and discover any issues fast.
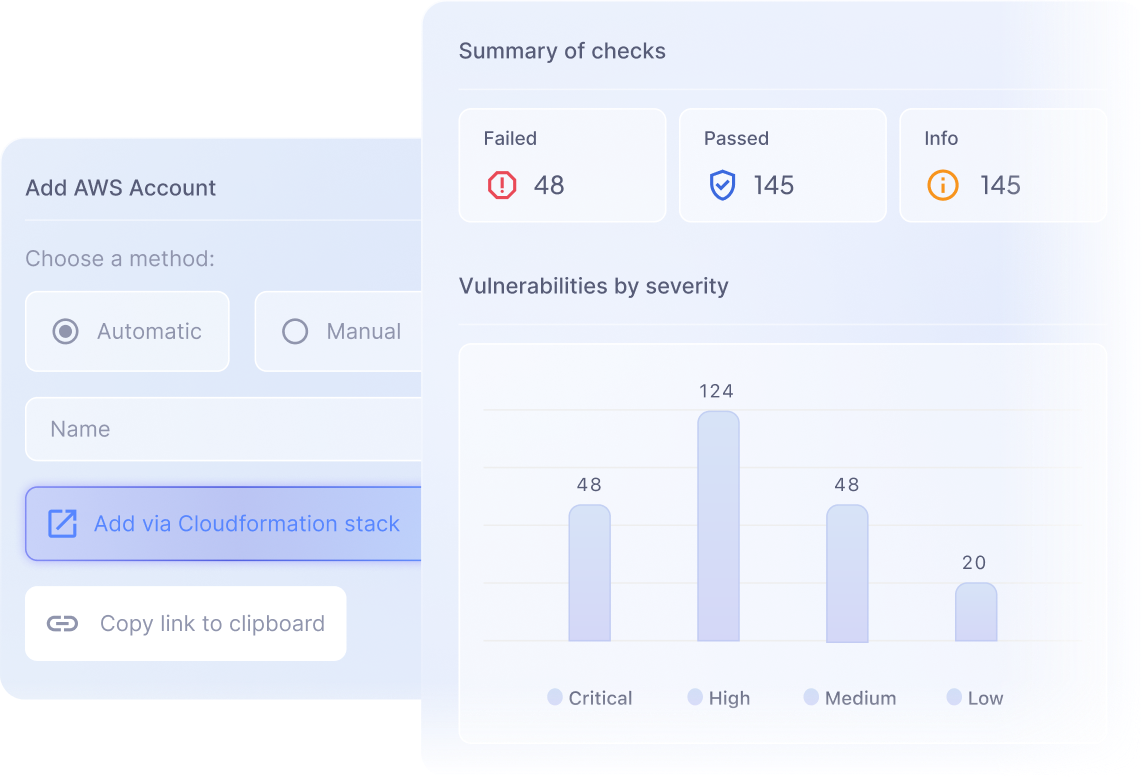
Cloud Security
Examine, analyze, and assess your cybersecurity in your cloud infrastructure. Identify all of your potential threats and obtain actionables, all in one place.

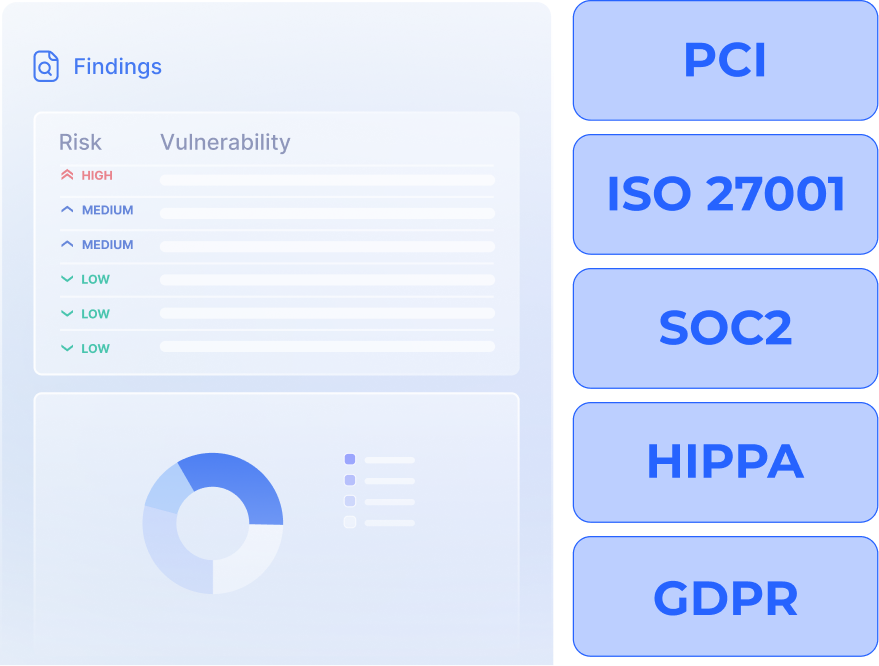
Alignment with compliance
Improve your organization's cloud infrastructure security to be in line with compliance standards such as PCI, GPDR, SOC2, HIPAA and ISO27001.
Real-time examination
Detect security threats in your cloud environment with our automated scans. Address your vulnerabilities in real-time.
Continuous surveillance
Don't lose any track. Monitor your AWS resources continuously and be aware of changes in your infrastructure.
Phishing Monitor
Scan over your domain and find which malicious URLs on the internet could potentially target your users for phishing attacks. See them all in one place.
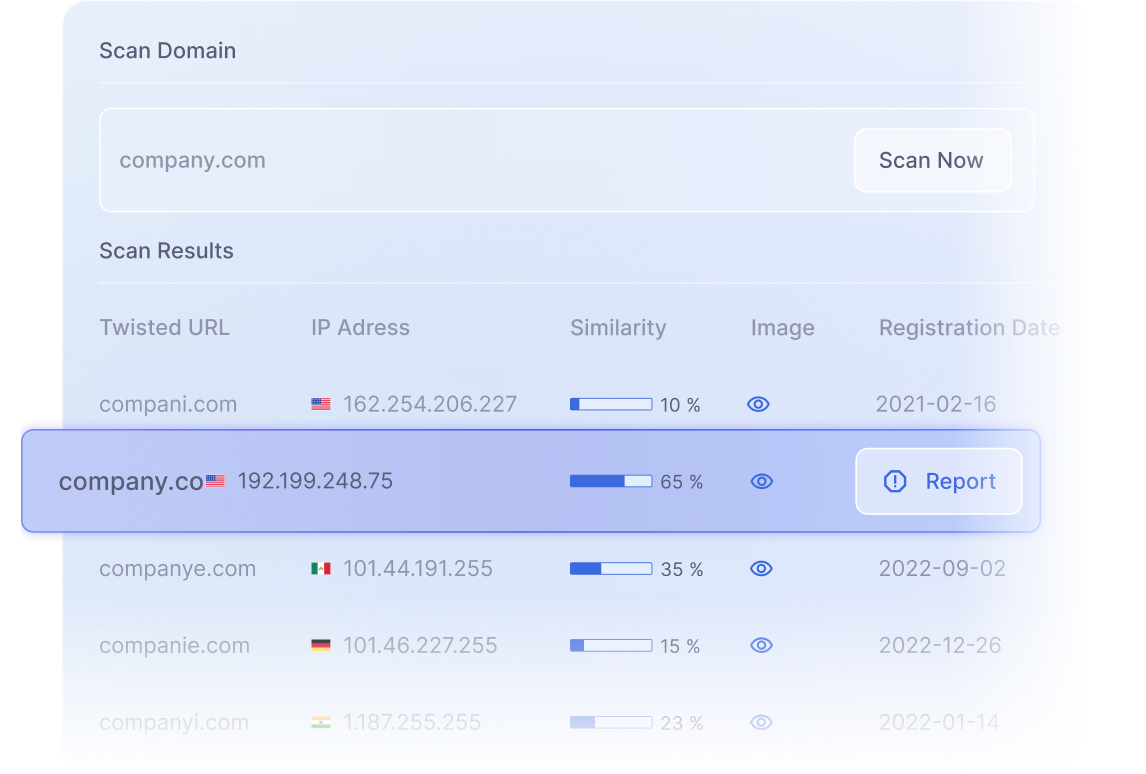

Detailed information
Get relevant information about all the malicious domains found, such as their IP address, registration provider, mail server, and status.
Similarity by percentage
Don’t leave with any doubts. See how the malicious URLs that were found are similar to your domain by percentage.
Clear timeframe
Check out when the malicious URLs were discovered and last seen.
Pentesting
Prepare for Pentesting
Use Strike’s security stack before, during, and after every pentest to get better results.
Pentesting augmented by technology
Complement your pentest with the power of Strike’s security stack to get x3 better results. With all the information about your findings in a centralized platform, your Striker can be more efficient and find the most interesting vulnerabilities.


Know the Strikers
Work with world-class ethical hackers, that are ready to test your platform. Even more important, get to work with the right match according to your tech stack, your industry, and even your time zone or language.
Learn more about the Strikers
The most advanced pentesting platform
Not only will you work with the best ethical hackers, but they will do it through an innovative SaaS platform. Set up your pentest in minutes, get the right striker assigned, and change the scope as needed - as many times as you want.


A report that is always waiting for you
Instead of asking for a report at the end of your pentest, you can download it anytime you want. The report is automatically generated with all the findings your strikers have reported. Use it to help your company get through compliance processes.

Testimonials
“Working with Strike was an excellent experience for us. We were able to create our own pentests and change their scope each month. The Strikers are world-class professionals who provide us with relevant findings quickly and efficiently. Also, automated tools like Phishing Monitor are really interesting for our company, because they help us spot fake domains trying to impersonate PedidosYa.”


Eduardo Gimenez
Chief Information Security Officer
“Working with Strike is extremely important to us, especially because they deliver quality work over our products in a continuous way, and provide constant follow-up when it comes to managing the already found vulnerabilities. Moreover, they are constantly making improvements in their SaaS platform so we can have the best experience possible. In case we have a problem, they listen and help us. That’s invaluable.”


Ileana Barrionuevo
Sr. Application Security Engineer of SDI-RED Team
“For us at pier, security is the most important aspect, not only on the surface but throughout our entire product. When we reached out to Strike, we were looking for someone that could test & find vulnerabilities across our entire stack. We are very happy that we have found the right partner to achieve that, and we are looking forward to continuing this important work together.”


Andras Hejj
CEO & CTO
Start now
Get ready for your next pentest
Planning for a Pentest soon? Schedule a demo with our technical team or try our security stack for free
