Strike’s CTEM AI Platform, powered by autonomous agents and strengthened by real security experts
Continuous Threat Exposure Management that unifies discovery, threat emulation, and remediation support — delivering visibility, speed, and real resilience across your entire digital perimeter.

Built for organizations that need continuous, end-to-end threat exposure management
Security teams that require real-time visibility over every digital asset, and automated testing triggered by every change.
Companies that need autonomous exposure discovery and instant validation the moment new risks emerge — not weeks after a scheduled assessment.
Organizations looking to accelerate remediation with guided workflows, real-time retesting, and compliance-ready insights in one unified platform.
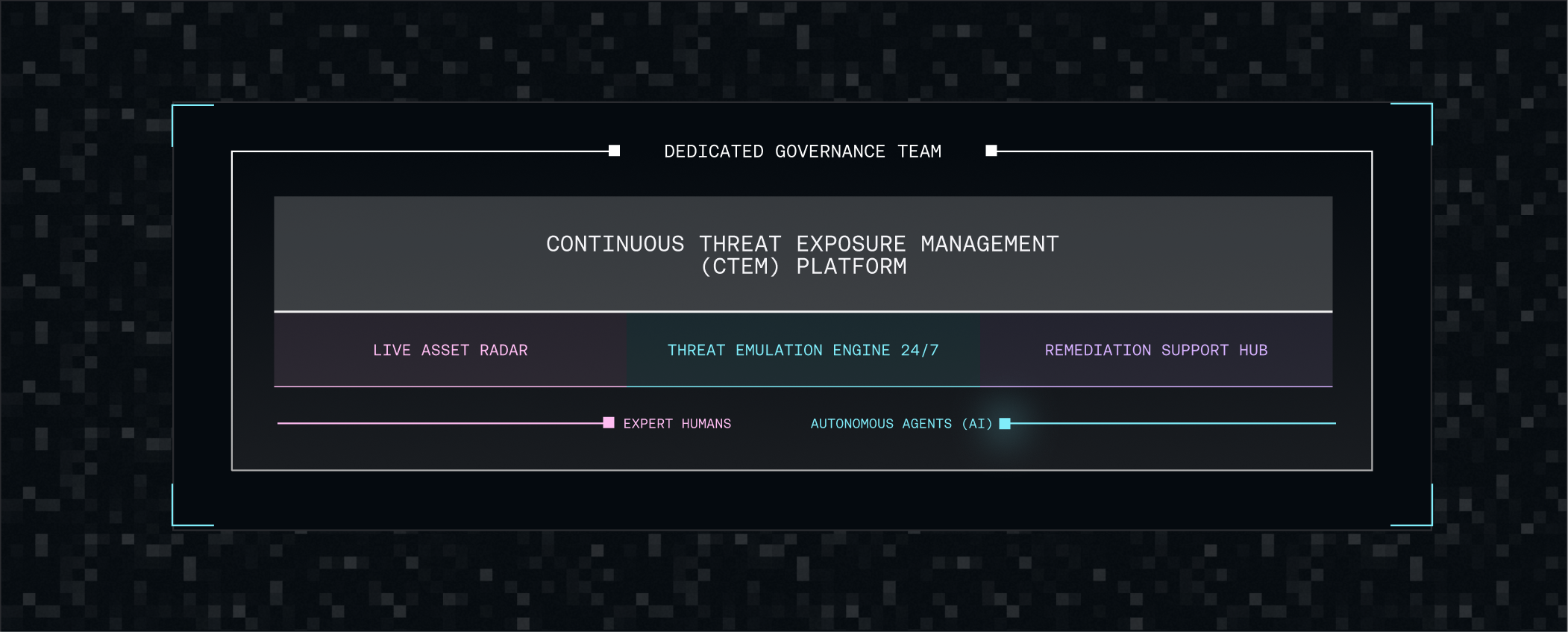
Our solution architecture
A centralized platform that unifies Live Asset Radar, 24/7 Threat Emulation, and the Remediation Support Hub—powered by a dedicated governance team, autonomous AI agents, and security experts.
STRIKE CTEM PLATFORM
Beyond testing. A strategic system for continuous exposure control.
Strike’s CTEM Platform helps you understand, challenge, and reduce your exposure with real-time intelligence, autonomous attack emulation, and fast, guided remediation.

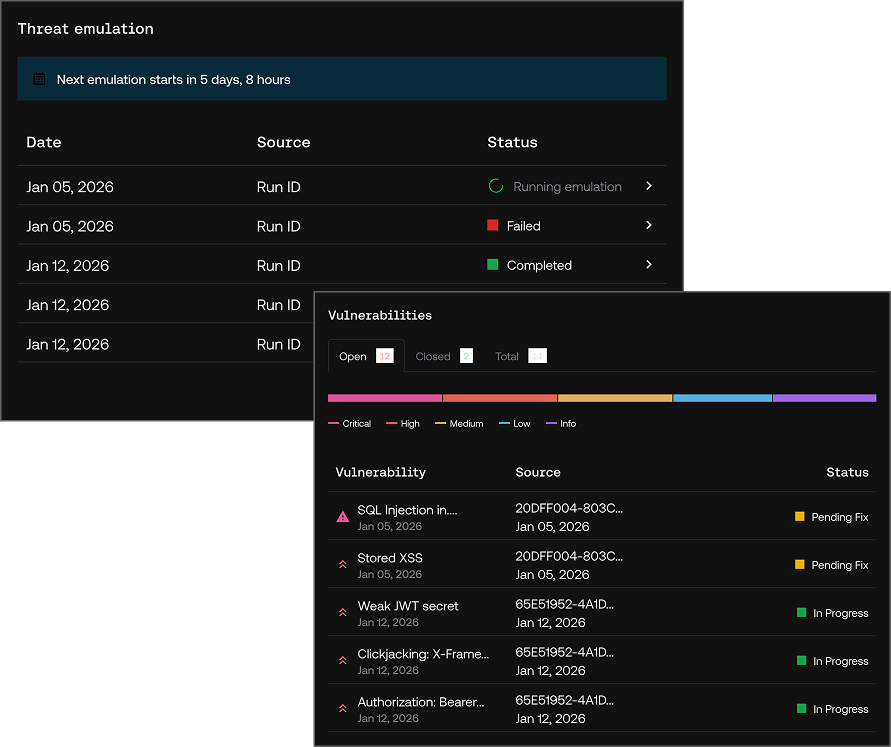
In-depth continuous testing
Strikers uncover high-impact vulnerabilities across multi-technology environments (web apps, APIs, mobile, cloud, and more).

AI-led retesting on-demand
Validate fixes instantly, without waiting for the next testing cycle.

Real-time fixing
AI agents guide your team step-by-step through remediation to accelerate resolution.

Step-by-step Threat emulation creation
Easily scope, launch, and track your Threat emulation with full transparency.

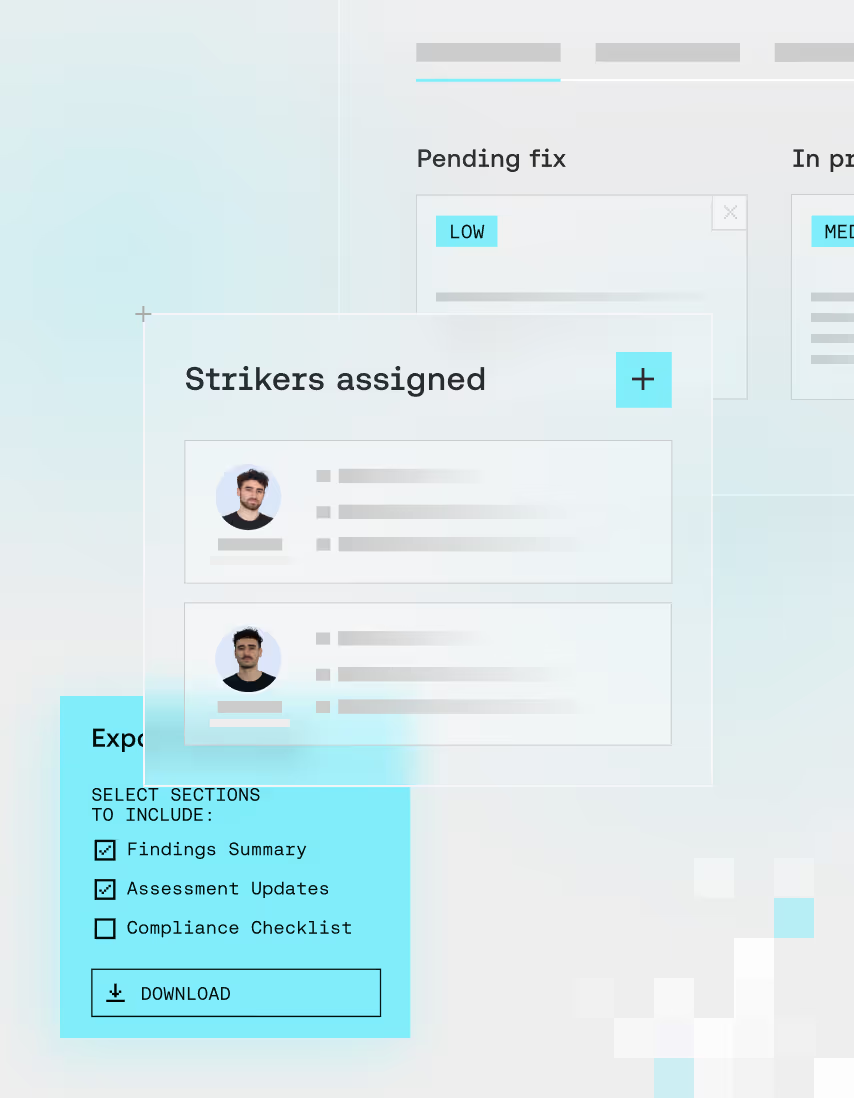
Human triaging & peer review
Every finding is validated by security experts to ensure accuracy and impact.

Full visibility
Track every finding with complete transparency through security expert work logs and real-time notifications.

Seamless integrations
Connect directly with Slack, Teams and Jira to streamline collaboration with your security and development teams.

Vulnerability Manager
Visualize, manage, and retest vulnerabilities in one platform, with full context on severity, sources, and remediation.

Compliance-ready reporting
Automatically generate up-to-date reports aligned with PCI DSS, HIPAA, ISO 27001, SOC 2, and more.

Ongoing partnership
Weekly check-ins with a dedicated Customer Success Manager, plus personalized onboarding and strategic planning.
With Strike CTEM Platform, you don’t just get a security test, you gain a strategic partner to strengthen defenses, accelerate remediation, and achieve compliance with confidence.
Trusted by security teams that lead
Human expertise.
AI power.
Superior security.
Whether you’re scaling fast, closing enterprise deals, or just tired of noisy reports, we’ll help you build a security stack that moves faster than your threats.