An always-on discovery layer that combines AI speed with human expertise
Continuous Hybrid Testing enhances the CTEM Platform with an additional layer where autonomous agents and expert researchers work in parallel to uncover deeper exposures, validate complex scenarios, and expand coverage across your entire digital environment. It’s human-led testing, boosted by AI, that keeps your exposure discovery and validation cycles continuously active.

The hybrid layer built for enterprise-grade continuous testing
Continuous exposure testing reaches its highest potential when AI agents and human experts work together. This hybrid layer delivers the scalability enterprises need without sacrificing depth or precision.

Reconnaissance
The attack surface gets analyzed and attack scenarios are predicted.

Threat Emulation
Autonomous agents and human experts replicate real-world behaviors to identify meaningful exposures.

Triaging
All findings are reviewed by our hacking governance team before being reported.
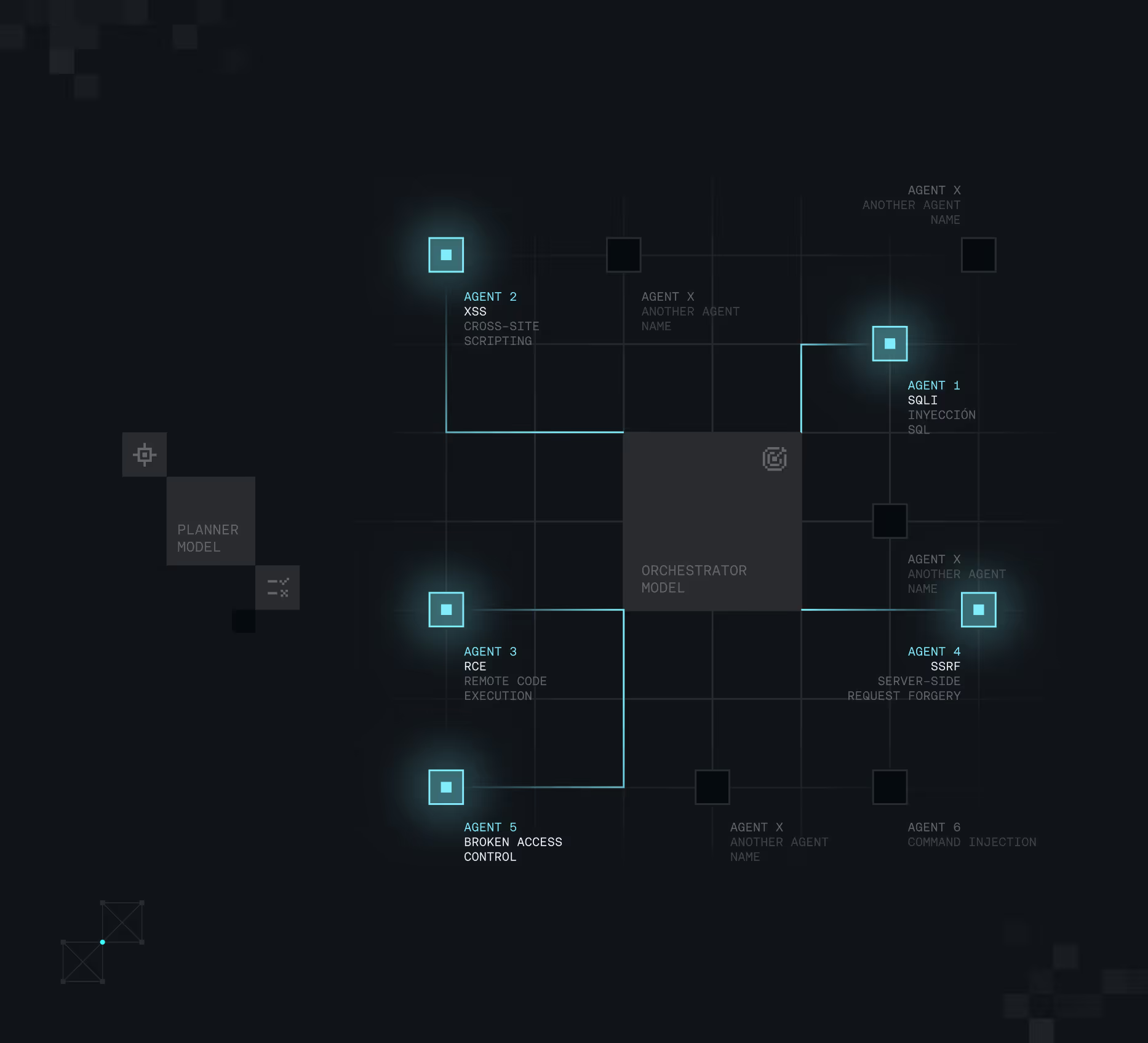
The architecture that runs the show
An open look at how our models operate to get the best results. Strike’s AI architecture consists of three major pillars:
The Planner
The Planner senses and monitors any surface to determine the most reasonable testing strategy, including business-logic attack vectors.
The Orchestrator
With that plan in place, the Orchestrator Model guides the execution of the Autonomous Agents.
The Autonomous Agents
Each agent looks up for one specific type of vulnerability, which is the key for having the most scalable architecture.



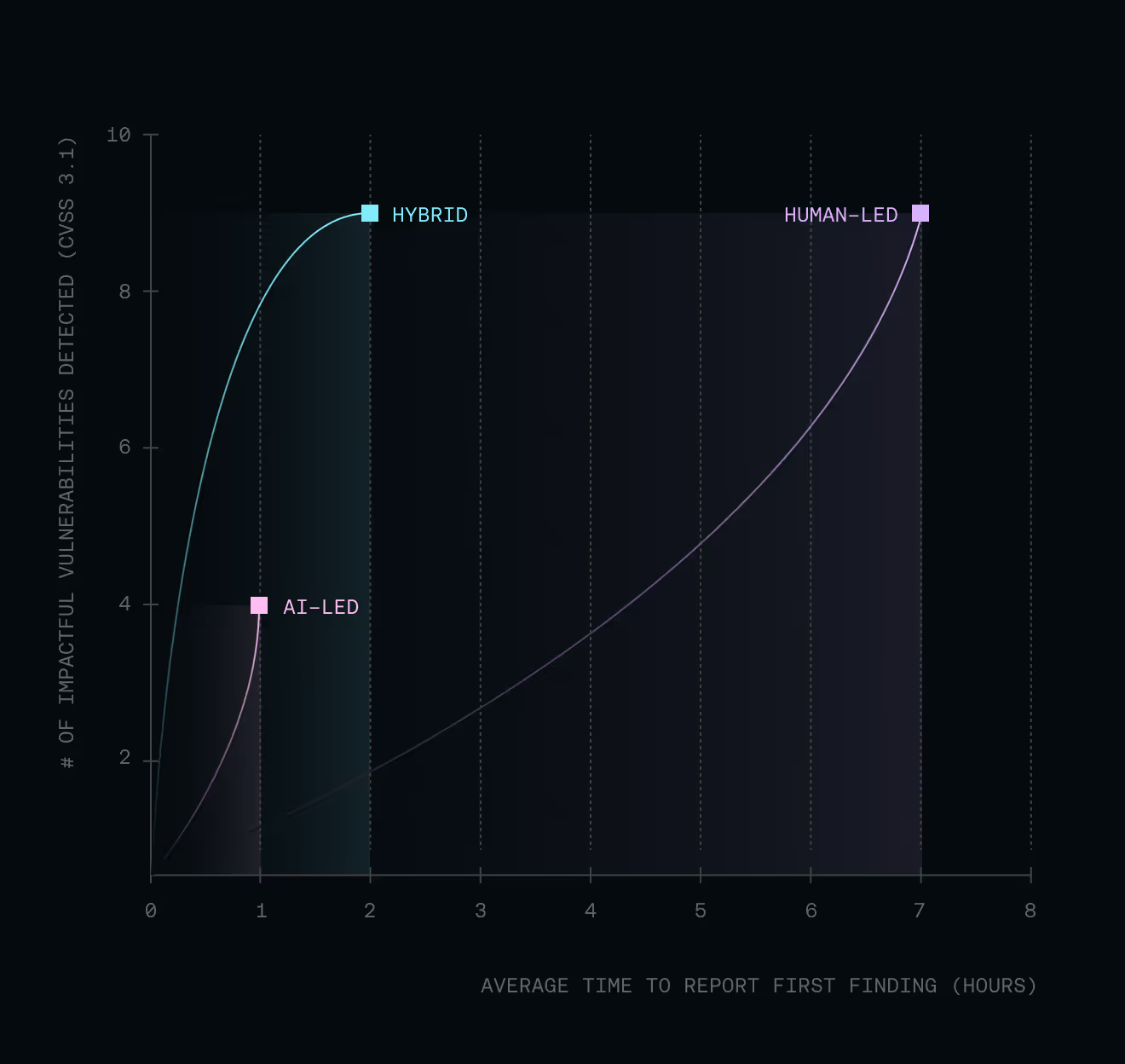
The hybrid advantage: scale, depth, accuracy
Scaling offensive security becomes possible when AI and human intuition work in parallel to validate complex scenarios and strengthen detection.
Operational efficiency
Optimize internal resources, eliminating as many manual processes as possible, and letting humans just test the attack vectors the agents still can't.
Real continuous security
Monitor consistently the attack surface with the help of the Planner Model to plan your next Attack Simulation.
Reduction of Mean-time-to-remediate
Resolve every finding with ease thanks to fix suggestions, and run AI-retesting for every finding.
Problem-solving skills for business-logic vulnerabilities
The AI models guided by our security experts are capable of finding industry-specific vulnerabilities.

Excessive trust in user actions

Flawed session management

Price manipulation

Privilege escalation

Unauthorised data access

Improper access controls

Abuse of system workflows

Authentication bypass
Know the agents and how they operate
Attack Simulations are executed by autonomous agents, each one testing for a specific vulnerability.
Reflected XSS
The agent identifies reflected cross-site scripting flaws that allow attackers to inject malicious scripts through URLs or parameters visible in the browser.
SLQ Injection Error based
Detects SQL injection vulnerabilities that expose database errors, allowing attackers to retrieve sensitive information through manipulated queries.
Stored XSS
Finds persistent XSS vulnerabilities where malicious scripts are stored in the application and executed every time the affected page is loaded.
SQL Injection Union-based
Searches for SQL injection flaws that use the UNION operator to extract additional data from different database tables.
DOM-based XSS
dentifies client-side injection vulnerabilities that occur within the browser’s DOM environment, often bypassing traditional input validation.
IDOR (Insecure Direct Object Reference)
Detects authorization flaws that allow attackers to access or modify objects (such as user data or files) without proper permission.
Authentication bypass XSS
Finds weaknesses in authentication flows that allow attackers to gain unauthorized access to systems or accounts.
Built for scale.
Powered by experts and AI.
Capabilities that can only be reached by going hybrid
Attack Simulation Request Platform
Personalize your tests to the details by matching your needs. Add your assets once and they will be ready to be tested forever.
AI controllers
Supervise your experience by adjusting Intensity, Flexibility, Aggressiveness and Creativity.
Auto-generated PDF Report
Your report is generated in real-time, right when you need it. Select its content and language for maximum personalization.
AI-led retesting for every finding
Retest any specific vulnerability within seconds to check if it's still there. This option is also available for human-led findings.
Always-on Attack Simulation
Integrate your stack so every new feature deployed can be tested as soon as it hits production.
Trusted by security teams that lead
Human expertise.
AI power.
Superior security.
Whether you’re scaling fast, closing enterprise deals, or just tired of noisy reports, we’ll help you build a security stack that moves faster than your threats.








