Strike in numbers
Key metrics that define our impact
in risk mitigated
Potential losses avoided through critical vulnerability discovery and breach prevention.
critical vulnerabilities reported
Validated security findings with detailed impact analysis and remediation steps.
more efficient than human-led testing
AI-led attack simulations cover in 1 hour what humans achieve in 3 days.
The AI platform for Continuous Threat Exposure Management
Stay ahead of threats with our platform that maps your assets, tests them continuously, and accelerates remediation across your entire environment.
[Live Asset Radar]
Real-time visibility of every asset
Discover and monitor all your organization’s assets in real time. Optimize your security team’s time and visibility.


[Threat Emulation Engine 24/7]
Perpetual testing across all mapped assets
Autonomous, continuous testing that discovers and validates exposures the moment they appear.


[Remediation Support Hub]
Faster vulnerability resolution with end-to-end support
Guided remediation workflows, automated retesting, and expert-validated insights that help teams fix issues faster and stay audit-ready.


Boost your results with expert triaging & hybrid testing
Automation to cover more. Experts to validate what matters.

AI-led discovery


Hybrid Boost
(AI + security experts)


Expert Triage
Precise, actionable findings, with zero noise


What makes Strike different
From precision testing to predictive analysis, these are the capabilities that set Strike apart.
Map every asset. Secure every change.
Strike’s AI agents map your entire attack surface and test it daily with expert-level precision.
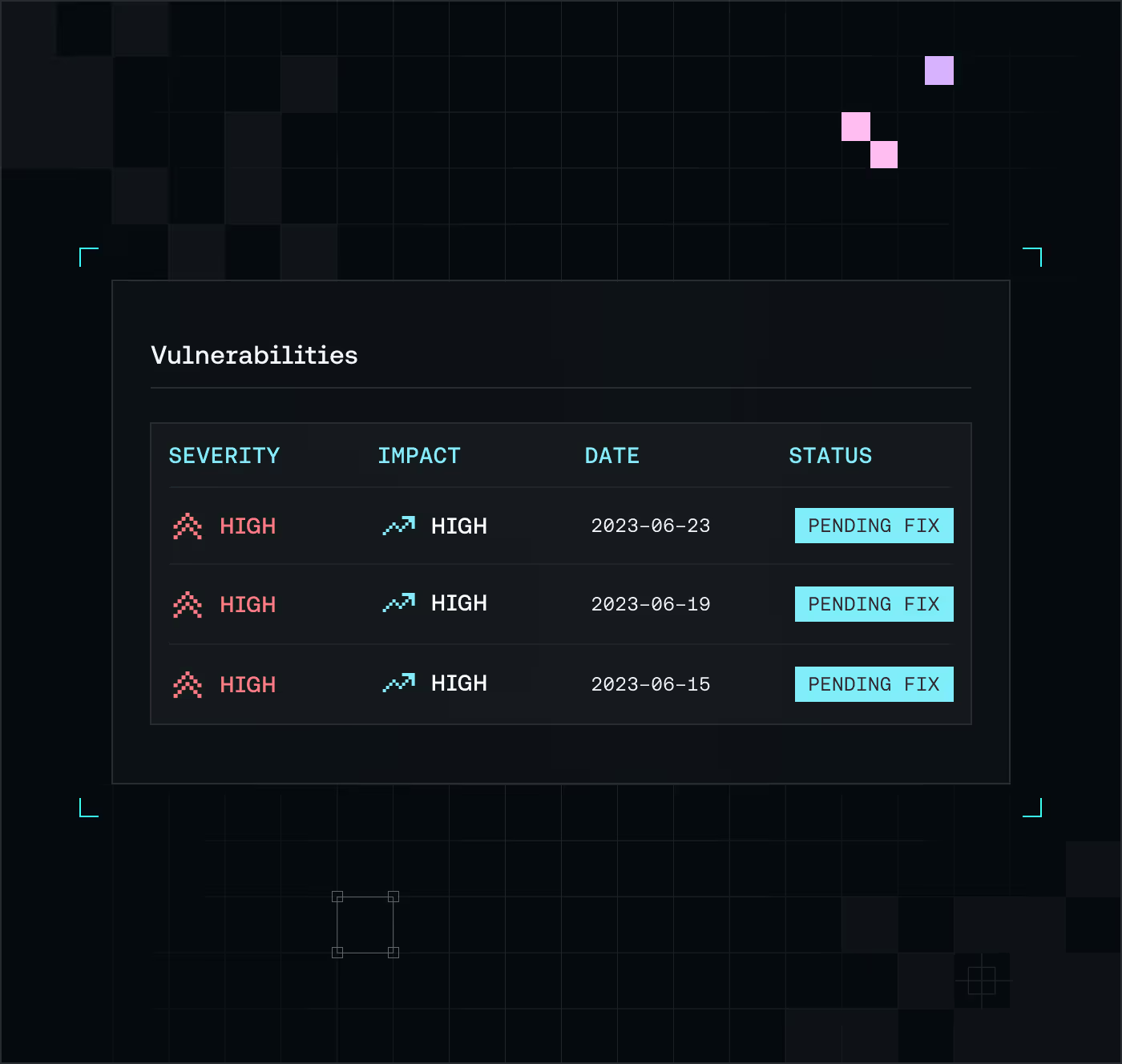
Discover what's hidden — automatically.
Continuously map every asset across your environment, surfacing exposures before attackers ever can.
Test every day, with expert precision.
AI-led attack simulations adapt to each change in your web and infrastructure, mirroring top security experts at machine speed.
Fix smarter, right at the code.
Receive actionable remediations directly in your repositories, closing the loop from detection to prevention.
Industries
Strike operates where risk hits hardest
Targeted security. Industry by industry.
Trusted by security teams that lead
Recognized by the industry.
Backed by results.
From independent evaluations and analyst reports to awards and client recognition, see how Strike is earning trust across the cybersecurity ecosystem.
Human expertise.
AI power.
Superior security.
Whether you’re scaling fast, closing enterprise deals, or just tired of noisy reports, we’ll help you build a security stack that moves faster than your threats.

Resource Hub




























































