Speed up your offensive security flows from weeks to hours
Strike’s AI agents are both powerful and precise, executing their tests at the highest pace. The models are trained on real-world data from ethical hacking exercises performed over years of work, which leads to the understanding of specific business flows and attack vectors.

From discovery to exploitation, learn how our AI-led testing works
Secure your system at deployment speed

Real continuous Attack Simulation
Start your attack simulation in seconds and get results in hours. Make offensive security part of your deployment cycle.


Business-ready
AI-led Attack Simulation is trained to find business-logic vulnerabilities as it understands every major industry.


Specific retesting
Validate if a vulnerability still exists, one by one, as many times as needed.


Maximum control
Adjust the variables that determine how your Attack Simulation works: Intensity, Flexibility, Aggressiveness and Creativity.


Open-by-design
Get to see the Autonomous agents in action to discover how your tests are being performed.

The architecture that runs the show
An open look at how our models operate to get the best results. Strike’s AI architecture consists of three major pillars:
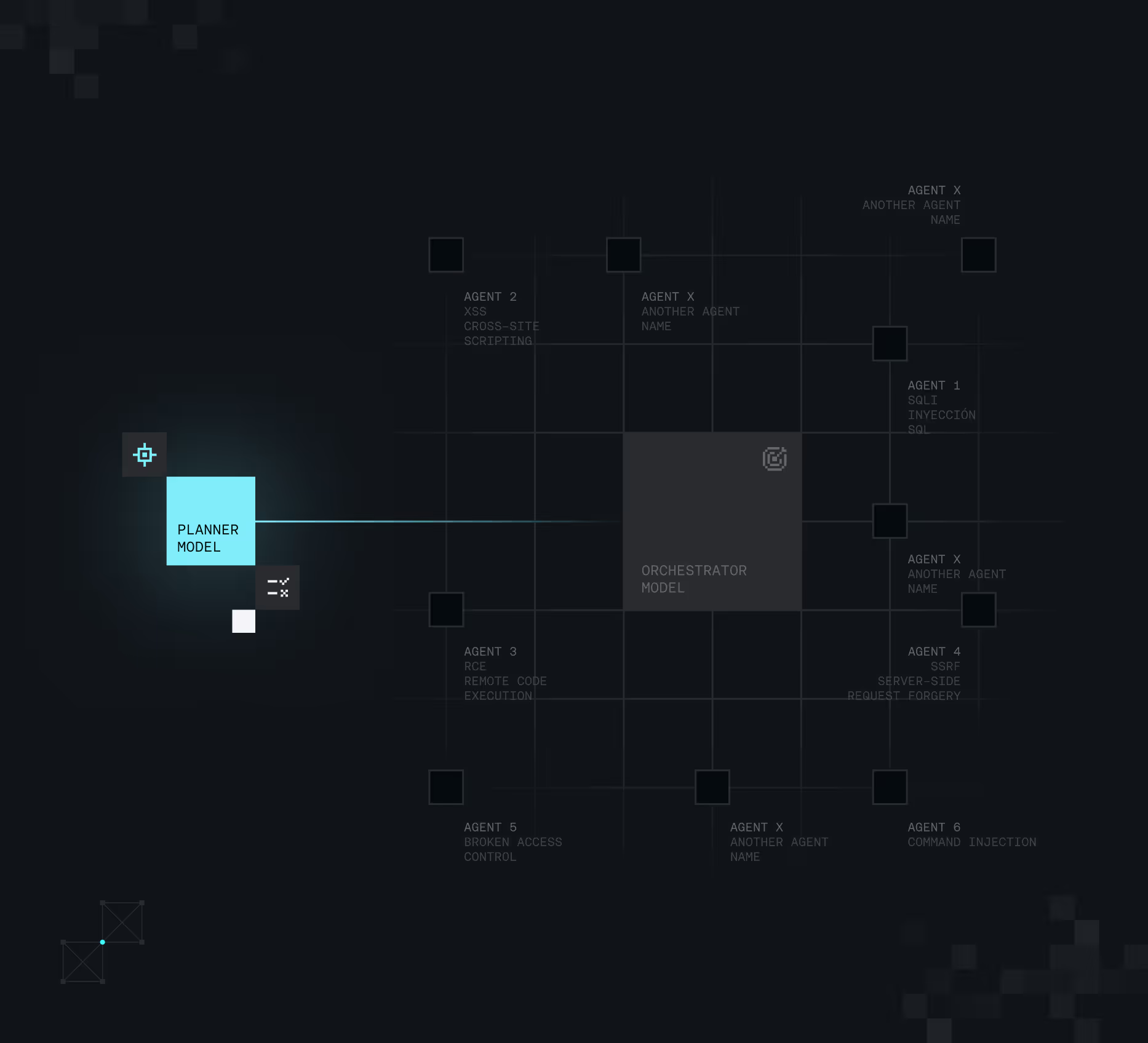
The Planner
The Planner senses and monitors any surface to determine the most reasonable testing strategy, including business-logic attack vectors.
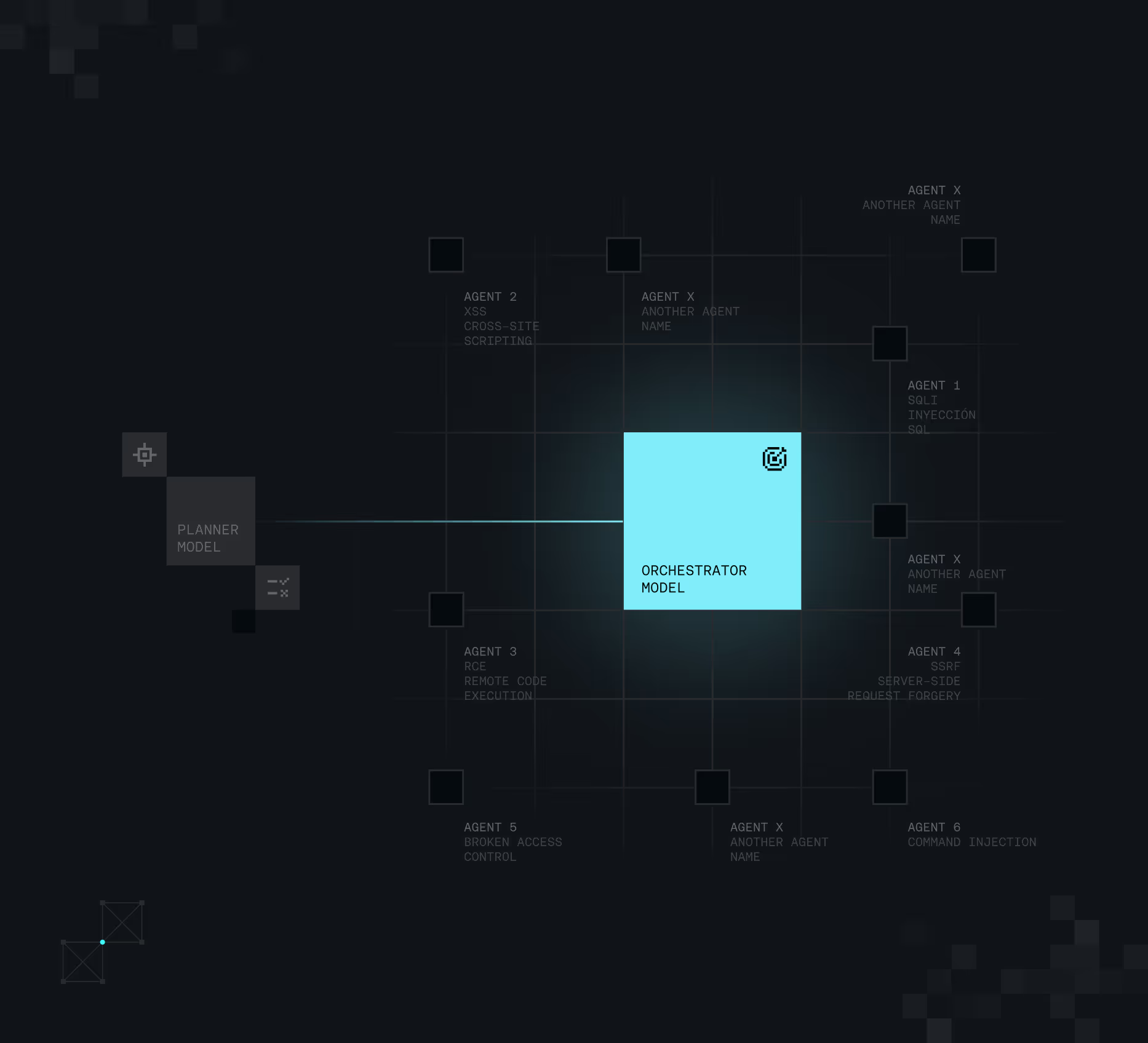
The Orchestrator
With that plan in place, the Orchestrator Model guides the execution of the Autonomous Agents.
The Autonomous Agents
Each agent looks up for one specific type of vulnerability, which is the key for having the most scalable architecture.
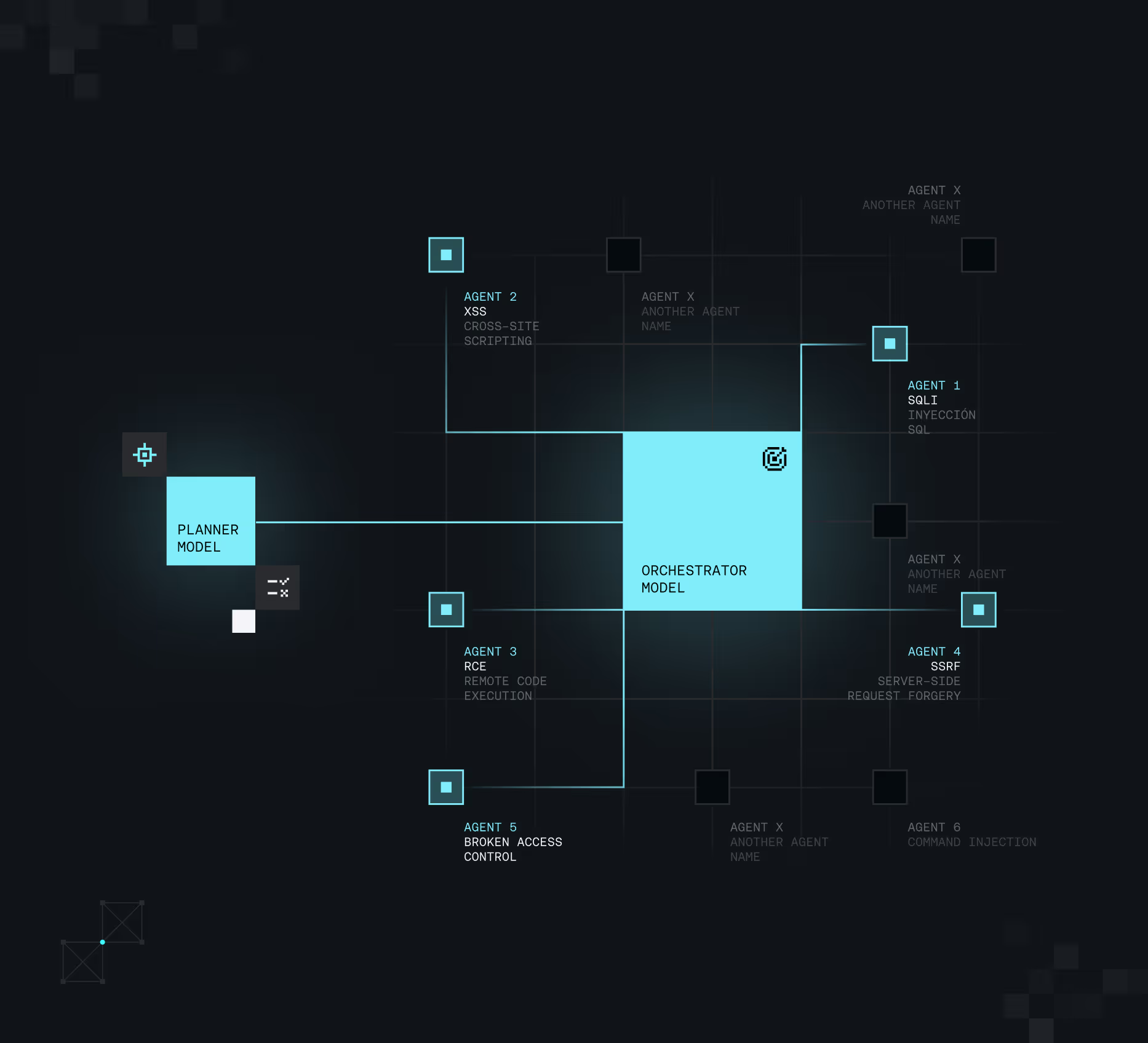
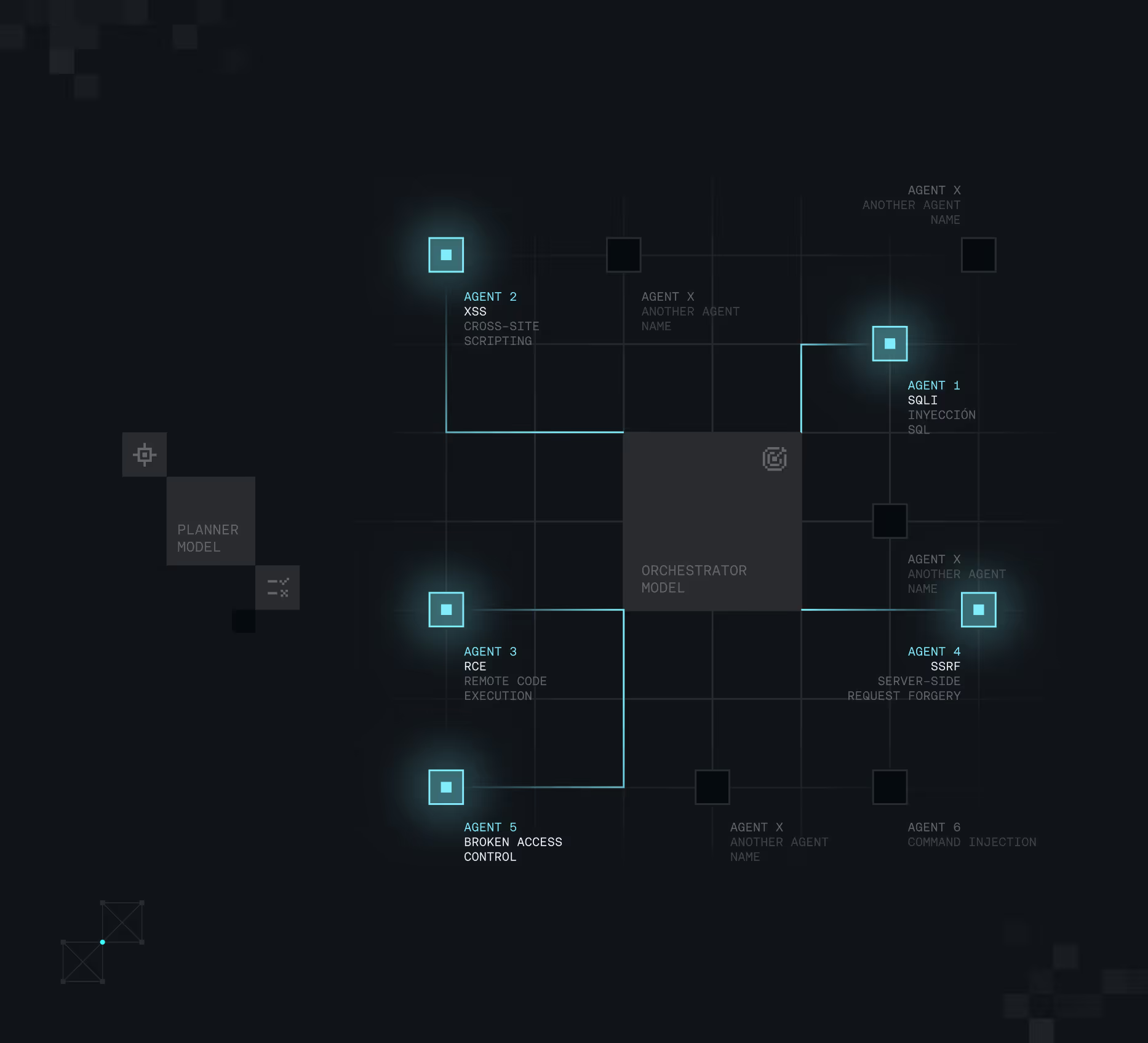
Know the agents and how they operate
Attack Simulations are executed by autonomous agents, each one testing for a specific vulnerability.
Reflected XSS
The agent identifies reflected cross-site scripting flaws that allow attackers to inject malicious scripts through URLs or parameters visible in the browser.
SLQ Injection Error based
Detects SQL injection vulnerabilities that expose database errors, allowing attackers to retrieve sensitive information through manipulated queries.
Stored XSS
Finds persistent XSS vulnerabilities where malicious scripts are stored in the application and executed every time the affected page is loaded.
SQL Injection Union-based
Searches for SQL injection flaws that use the UNION operator to extract additional data from different database tables.
DOM-based XSS
dentifies client-side injection vulnerabilities that occur within the browser’s DOM environment, often bypassing traditional input validation.
IDOR (Insecure Direct Object Reference)
Detects authorization flaws that allow attackers to access or modify objects (such as user data or files) without proper permission.
Authentication bypass XSS
Finds weaknesses in authentication flows that allow attackers to gain unauthorized access to systems or accounts.
Human expertise.
AI power.
Superior security.
Whether you’re scaling fast, closing enterprise deals, or just tired of noisy reports, we’ll help you build a security stack that moves faster than your threats.



