Beginner’s guide to iOS pentesting: tools, setup, and techniques

Mobile applications have become a prime target for cyberattacks. Successful exploits can give attackers access to user credentials or enable malware installation—leading to stolen funds and compromised data. That’s why iOS pentesting is critical for businesses aiming to secure their mobile environments and protect users.
According to the 2023 HackerPowered Security Report by HackerOne, only 17% of security researchers have experience in iOS security. This skill gap makes iOS applications more vulnerable to attacks. To help bridge it, we’ve created this guide covering essential tools, jailbreak setup, and static/dynamic assessment methods for iOS pentesting.
Setting up your iOS pentesting environment
Before starting any tests, you’ll need the right toolkits. Mobile application security testing generally has two phases:
1. Static Assessment
Analyzing the app’s source code to find vulnerabilities.
Example tool: MobSF
2. Dynamic Assessment
Running and executing the app to detect security issues during runtime.
Example tools: Frida, Objection, Burp Suite
Jailbreak for iOS pentesting
Jailbreaking grants root access to an iOS device, bypassing manufacturer restrictions. This step is often required to install testing tools.
- Recommended jailbreak tool: Palera1n
- Supported devices: A11 chipset (e.g., iPhone X) or lower
Check if your device is jailbroken:
Look for the Palera1n app. If installed, you can manage tweaks using Sileo to support your pentesting setup.
Static assessment toolkit
Static assessments help uncover:
- Hardcoded secrets, API keys, and tokens
- API endpoints and exported components
- Permission models and binary checks
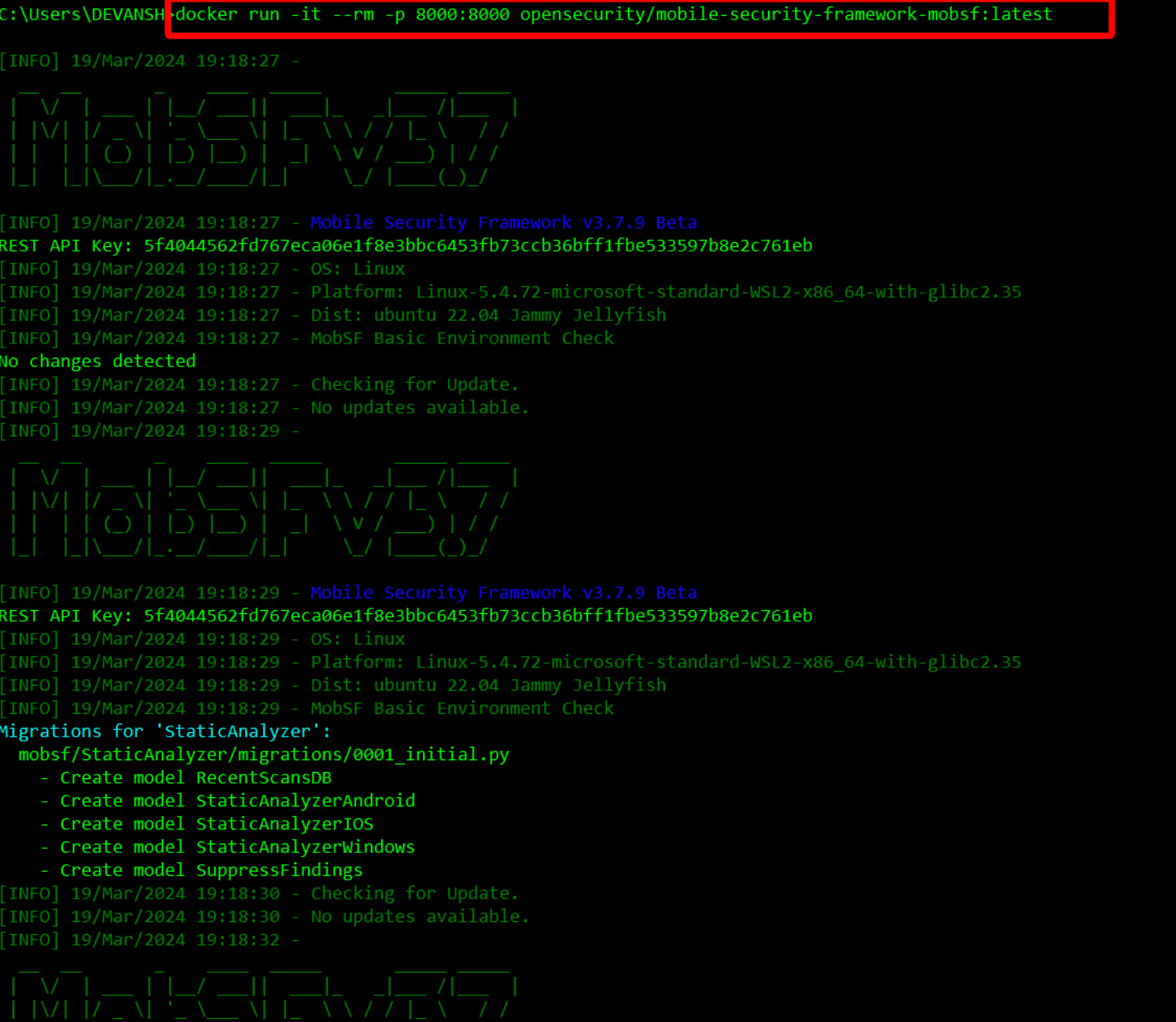
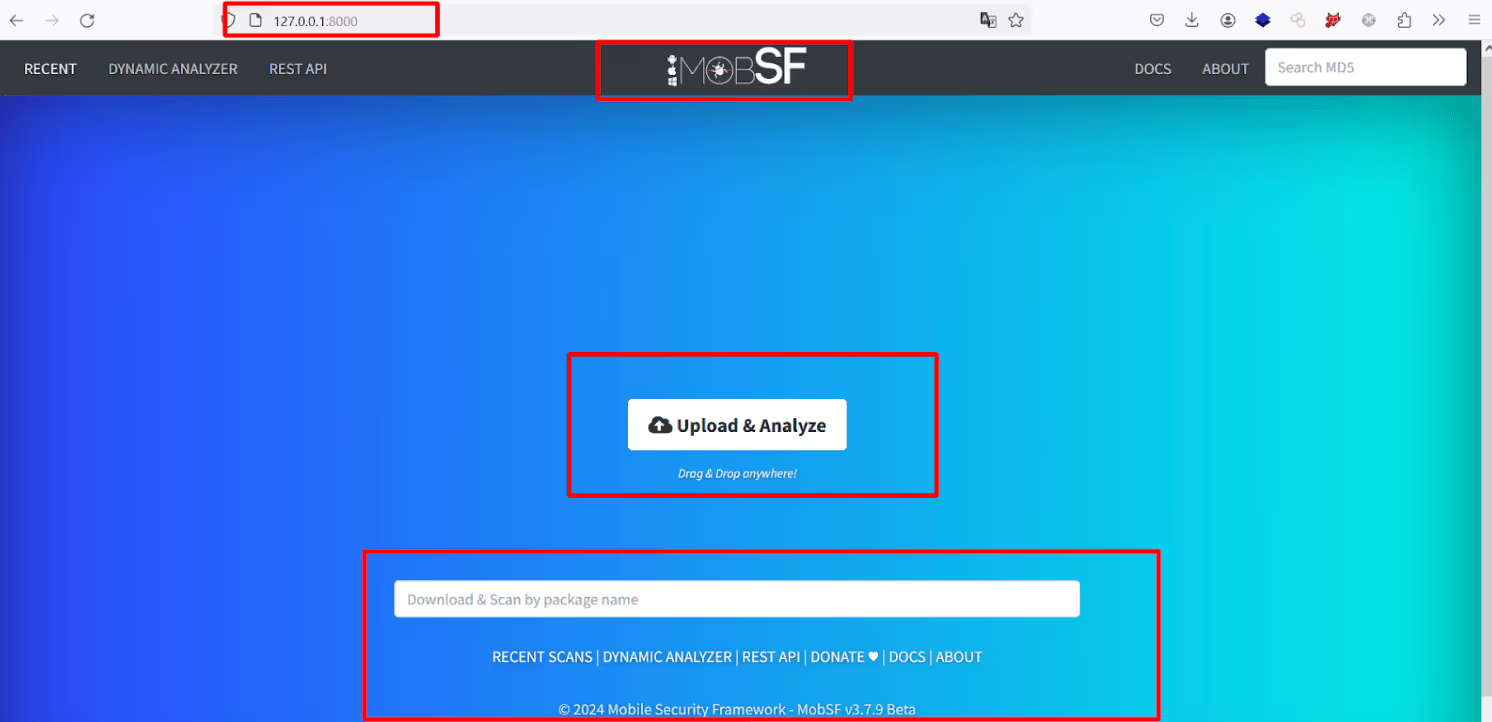
Tool highlight: Mobile Security Framework (MobSF)
- Supports Android, iOS, and Windows Mobile
- Analyzes APK, IPA, and APPX binaries
- Provides detailed vulnerability reports
MobSF benefits for iOS pentesting:
- Quick vulnerability detection before deployment
- Both static and dynamic analysis in one platform

Dynamic assessment toolkit
Dynamic testing focuses on hooking application logic to alter functionality or bypass restrictions.
Frida
- Dynamic instrumentation toolkit
- Inject scripts into app processes
- Bypass certificate pinning, root detection, and memory protections
Install Frida on a jailbroken iOS device:
- Open Sileo
- Go to Manage → Sources → Edit → Add
- Enter https://build.frida.re


4- Go to the newly added Frida source. 5- Install the Frida package.
Burpsuite
An integrated platform/graphical tool called Burpsuite is used to evaluate web applications for security. Its many tools function in sync to facilitate every step of the testing process, from the first mapping and analysis of the attack surface of an application to the identification and exploitation of security flaws. In Kali Linux, Burp Suite is installed by default.
The software was created by PortSwigger Web Security and is written in Java. There are three editions of the tool available: the Community Edition, which is available for free download, the Professional Edition and the Enterprise Edition, which has to be purchased following a trial period. There is a major reduction in functionality with the Community edition.
Burpsuite Installation:
1- Visit the given URL 2- Now, Click on Download and select Windows X64 host. 3- Finally, search for Burpsuite and create a New Project.
Using tweaks in iOS pentesting
These are third-party applications made for devices that have been jailbroken. They can add new features, tweak current functionality, or circumvent Apple's constraints.
Tweaks can be used in the context of iOS pentesting for a number of reasons, including:
- Around Jailbreak Detection: Certain applications limit their functionality or won't launch on smartphones that have been jailbroken. Testers can use tweaks to get around these security measures and use the app for testing. - Examining App Files: iOS devices often prevent users from accessing an application's internal files. Testers can check how the app saves data or operates by making changes to the file manager that give access to these files. - Monitoring Network Traffic: By allowing the data to be intercepted between an application and the internet, tweaks can assist find communication flaws in the programme. - Changing App Behaviour: A few adjustments make it possible to change an application's behaviour while it's being tested.
List of Common Tweaks:
1- Filza 2- Openssh 3- Frida 4- SSLBypass & SSL KillSwitch 5- AppStore++
Just now, you created your own playground for iOS pentesting. With the help of this personalised environment, you may analyse apps, find security holes, and eventually improve mobile security. But keep in mind that iOS security is a dynamic field. Updates to tools are made, new jailbreaks appear, and testing techniques continue to improve. Being at the top of your game is so crucial!
Here are some next steps to consider:
- Familiarise yourself with popular iOS pen testing tools like Frida, Objection, and Burp Suite.
- Explore resources for practice applications with known vulnerabilities like DVIA or iGoat.
- Stay updated on the latest iOS exploits and jailbreaks by following reputable security blogs and communities.
References
- https://kishorbalan.medium.com/start-your-first-ios-application-pentest-with-me-part-1-1692311f1902
- https://book.hacktricks.xyz/mobile-pentesting/ios-pentesting
- https://github.com/ivan-sincek/ios-penetration-testing-cheat-sheet
- https://www.yeswehack.com/learn-bug-bounty/getting-started-ios-penetration-testing-part-1
- https://www.yeswehack.com/learn-bug-bounty/getting-started-ios-penetration-testing-part-2