Hacking Web3: The security flaws you need to know (and how to prevent them)
.avif)
Web3 has revolutionized the digital landscape by offering decentralized solutions that promise greater user control, transparency, and security. However, with the growth of Web3 technologies comes a new set of security challenges. Understanding these vulnerabilities is crucial for developers, users, and organizations to ensure a safe experience in the decentralized web.
In this article, we’ll dive deep into the most common security vulnerabilities in Web3 and explore how they can be mitigated.
The Importance of Security in Web3
Web3 technologies, including blockchain, smart contracts, and decentralized applications (dApps), are transforming how we interact with the digital world. However, as with any new technology, they come with their own set of security challenges. Exploiting vulnerabilities in smart contracts or decentralized protocols can lead to severe consequences, including financial loss or loss of user trust. It's essential to understand these vulnerabilities and the best practices to mitigate them in order to build secure, reliable Web3 systems.
Next, we'll dive into some of the most common vulnerabilities found in Web3 applications, exploring how they can be exploited and what can be done to mitigate the risks they pose.
Common Security Vulnerabilities in Web3
Below is a list of the top 10 vulnerabilities in smart contracts, starting with the most popular one.
1. Front-running and Flash Loan Attacks
Front-running occurs when a malicious actor gains knowledge of a pending transaction and then executes their own transaction before the original one goes through, often taking advantage of market fluctuations.
Flash Loan Attacks involve taking out a large loan without any collateral, exploiting vulnerabilities in decentralized finance (DeFi) protocols. Attackers can use flash loans to manipulate prices, front-run transactions, or manipulate token values.
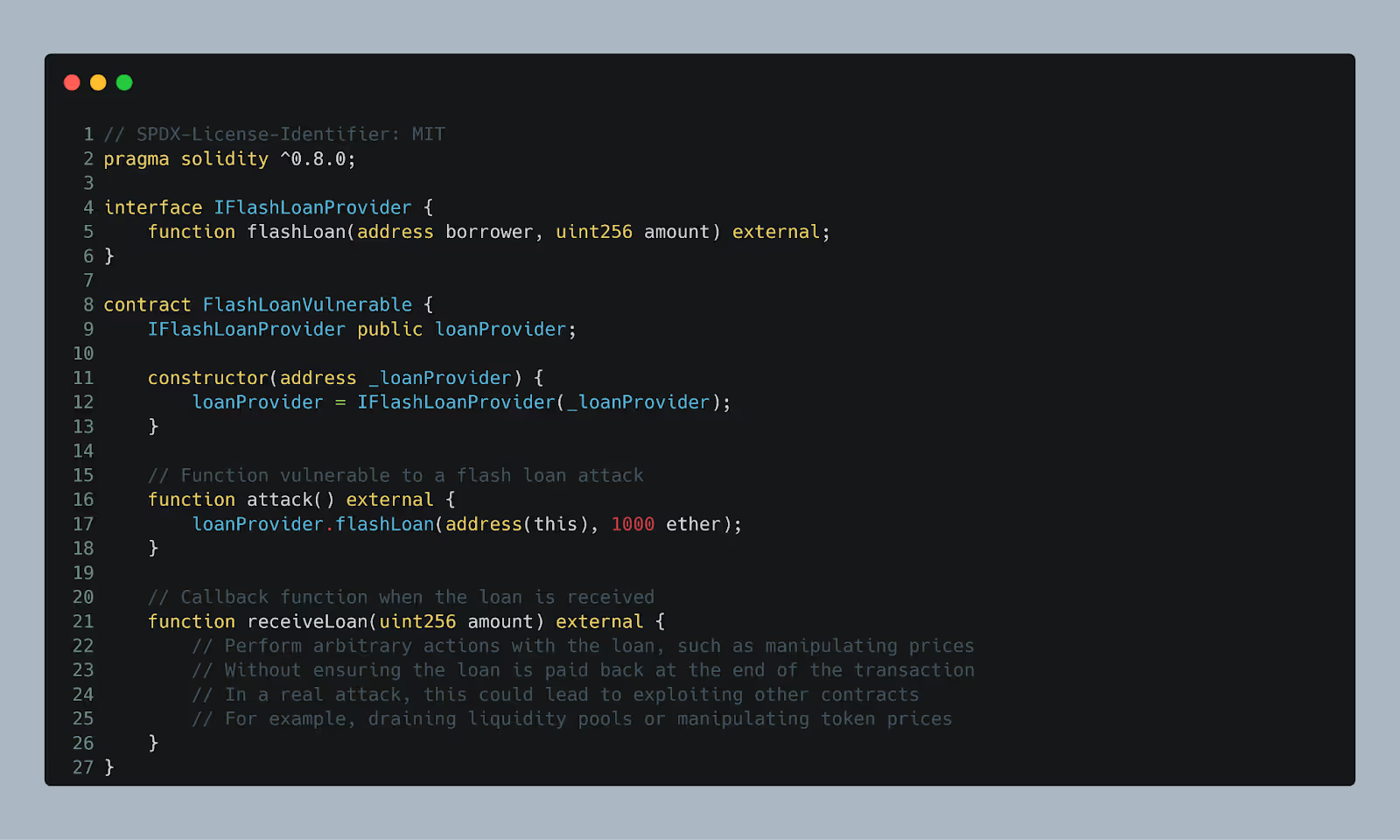
The contract allows borrowing tokens via a flash loan without ensuring the loan is repaid before executing other actions. An attacker can exploit this by borrowing tokens, manipulating prices or performing malicious actions, and then not repaying the loan, causing financial losses.
How to Mitigate:
- Use time delays or commit-reveal schemes in critical transactions to prevent front-running.
- Introduce slippage controls to prevent large price swings from affecting transactions.
- Monitor transaction patterns for unusual behavior that could indicate an attack.
2. Reentrancy Attacks: This occurs when a smart contract calls another contract, and that contract calls back into the original contract before the first one finishes executing. The most infamous case of this was the DAO hack of 2016, where attackers exploited reentrancy to drain funds.

An attacker can repeatedly call the withdraw() function before the balance is updated, draining the contract's funds. The state change happens after the external call, allowing reentrancy.
3.Cross-Chain Bridge Vulnerabilities
Cross-chain bridges allow for the transfer of assets between different blockchain networks, facilitating interoperability. While they serve as a crucial part of Web3, they also present several vulnerabilities.
Common Issues:
- Code exploits: Hackers can exploit vulnerabilities in the smart contracts that power the bridge, allowing them to steal funds or manipulate asset transfers.
- Lack of decentralization: Many bridges rely on trusted third parties, which can create centralization risks in an otherwise decentralized ecosystem.
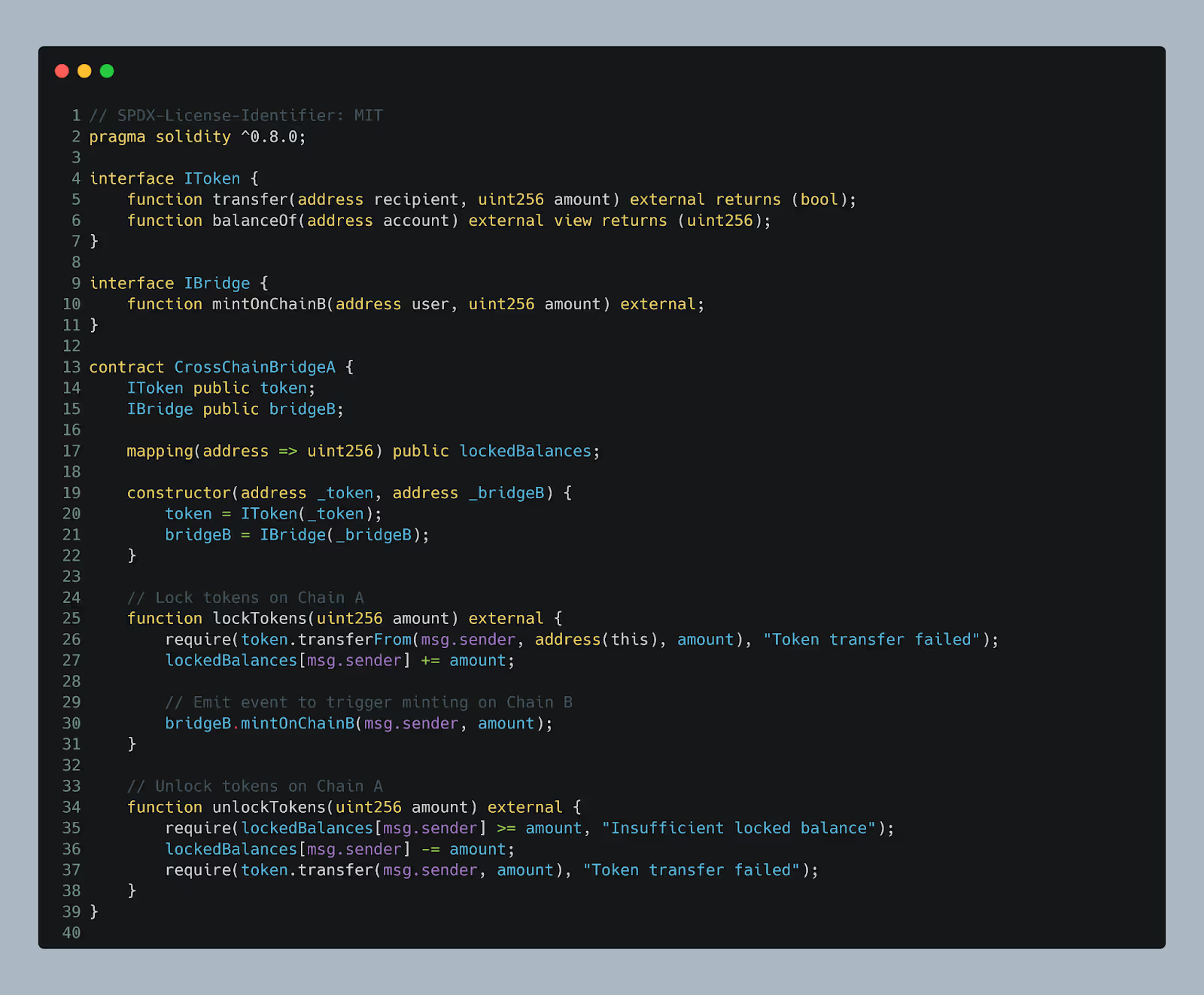
The vulnerability is a re-entrancy attack in the CrossChainBridge contract. When an attacker locks tokens on Chain A, the contract calls mintOnChainB to mint tokens on Chain B. However, due to the external call to mintOnChainB, the attacker can re-enter the lockTokens function before the balance is updated, allowing them to lock additional tokens without actually transferring any, leading to an inflated minting of tokens on Chain B.
How to Mitigate:
- Use decentralized and trusted bridge protocols.
- Regularly audit bridge smart contracts for vulnerabilities.
Consider adding multi-signature authorization and other security mechanisms to enhance bridge safety.
4.Vulnerabilities in Oracles
Decentralized oracles provide external data to smart contracts, allowing blockchain applications to interact with the outside world (e.g., fetching the price of a cryptocurrency). However, if oracles are compromised, it can lead to malicious contract execution or incorrect data being used in important decisions.
Common Issues:
- Data manipulation: Hackers can manipulate data inputs to smart contracts by targeting the oracle itself.
- Single point of failure: If an oracle service is centralized or uses a small set of data providers, it can become a target for attacks.
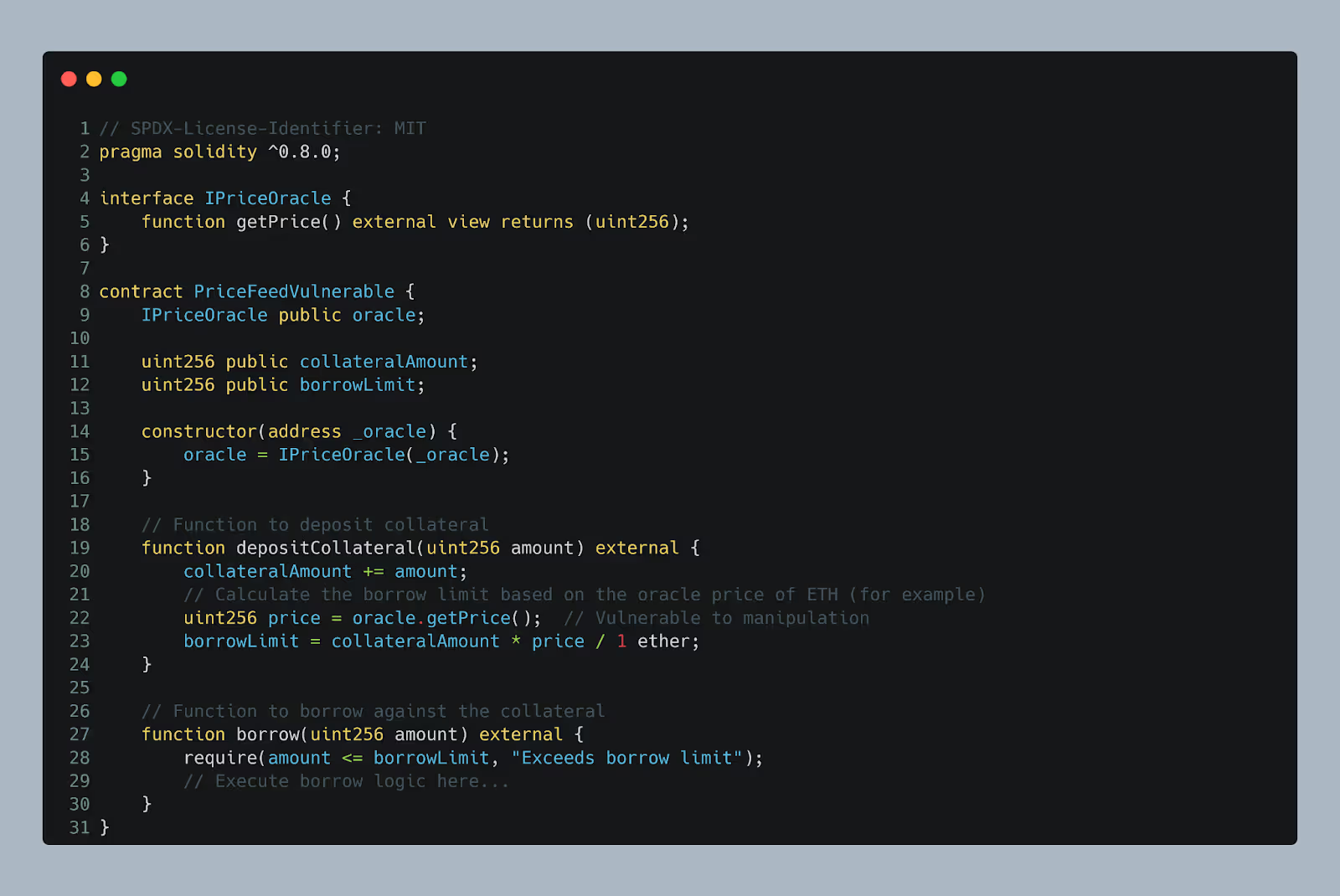
The contract relies on an external oracle to provide the price of the asset (e.g., ETH price in USD). The getPrice function from the oracle is used to calculate the borrow limit that a user can take based on their collateral.
However, this contract is vulnerable to manipulation because it blindly trusts the oracle's data without any verification or control. If an attacker can manipulate the price returned by the oracle, they can inflate the price of ETH, which would increase the borrow limit and allow them to borrow more than they should, potentially draining funds from the contract.
How to Mitigate:
- Use multiple data sources to ensure data integrity and reduce reliance on a single oracle provider.
- Employ decentralized oracle networks to distribute the risk and improve resilience.
5. Poor Tokenomics
Tokenomics refers to the economic model of a cryptocurrency or token. A flawed tokenomics structure can lead to various security issues, such as market manipulation, inflation, and unbalanced power dynamics.
Common Problems:
- Too much token concentration: If a small number of wallets hold the majority of the tokens, these actors can manipulate the market or vote on governance decisions unfairly.
- Unsustainable inflation: If a project’s tokenomics incentivizes too much token issuance, it can lead to hyperinflation and cause the token’s value to drop significantly.
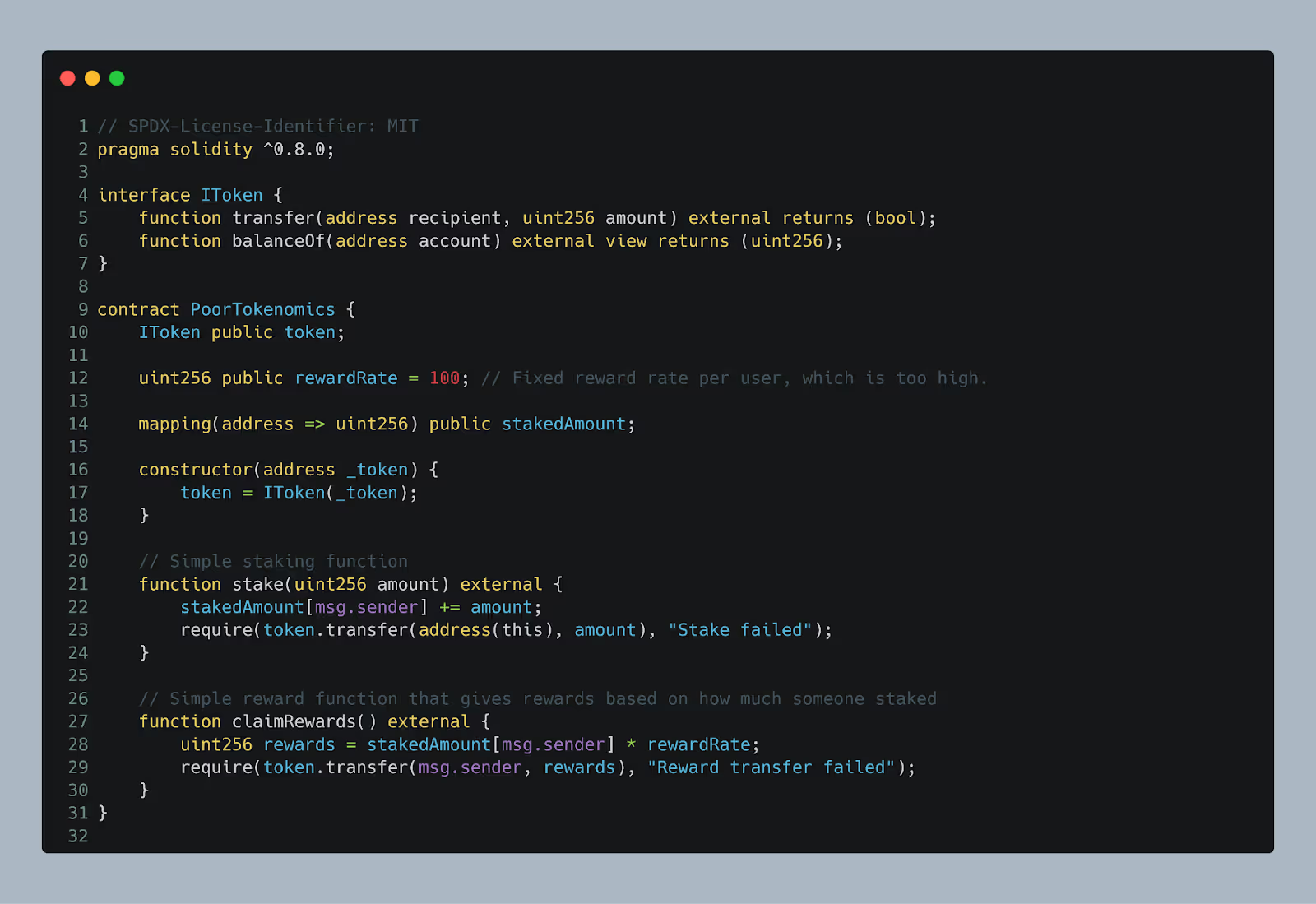
The vulnerability in this contract is poor tokenomics, as the reward rate is fixed and excessively high (100x the staked amount), which can lead to unsustainable inflation. This could quickly devalue the token, making it prone to collapse due to over-minting or excessive rewards being issued to users.
How to Mitigate:
- Design tokenomics with decentralization in mind, ensuring that no single entity or individual has too much control over the network or asset.
- Use vesting periods for token distribution to avoid dumping on the market.
- Monitor inflation rates and ensure that incentives align with long-term project goals.
6. Integer Overflow/Underflow: This happens when a variable exceeds its maximum or minimum value, causing unexpected behavior in the contract.

If a user has a very large balance and performs an operation that causes the balance to exceed the max uint256 value, it can overflow, or if they withdraw more than their balance, it can underflow, allowing for unintended behaviors.
7. Uninitialized Variables: Leaving variables uninitialized or improperly configured can introduce loopholes in the code.
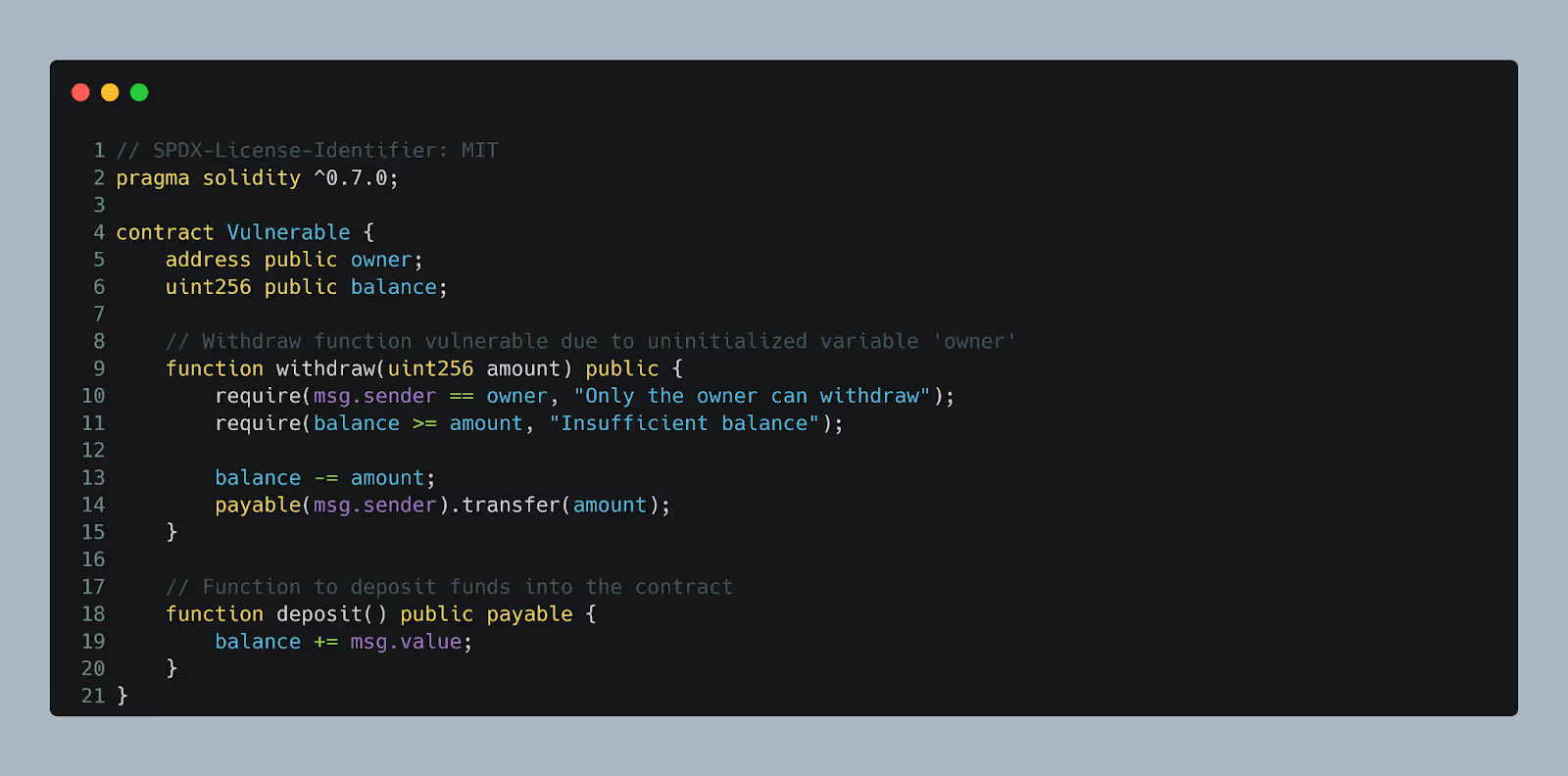
The owner variable is not initialized during contract deployment, so it defaults to address(0). This causes the withdraw function's msg.sender == owner check to always fail, preventing the withdrawal functionality from working as intended.
How to Mitigate:
- Always audit smart contracts thoroughly before deploying them on the blockchain.
- Use established frameworks and libraries that are well-tested and secure.
- Implement unit tests to check for vulnerabilities and edge cases.
8. Insecure Wallets
Web3 users typically store their private keys in digital wallets, but not all wallets are created equal. Insecure wallets, particularly hot wallets (wallets connected to the internet), are vulnerable to attacks.
Common Issues:
- Phishing and malware: Hackers can compromise wallet software through phishing schemes or by exploiting vulnerabilities in the wallet itself.
- Loss of keys: If a user loses access to their private keys, they lose access to their funds forever.
How to Mitigate:
- Use hardware wallets (cold storage) for long-term storage of assets.
- Enable multi-signature wallets for added security.
- Regularly update wallet software and always use trusted providers.
9. Phishing and Social Engineering Attacks
Phishing attacks are among the most common threats in Web3. These attacks typically involve fraudulent actors posing as legitimate entities to trick users into revealing sensitive information, such as private keys, wallet addresses, or seed phrases.
Common Tactics:
- Fake websites that mimic legitimate dApps or crypto exchanges.
- Scammers impersonating developers or influencers to solicit funds.
- Fake airdrops or giveaways that ask for users' private keys or personal information.
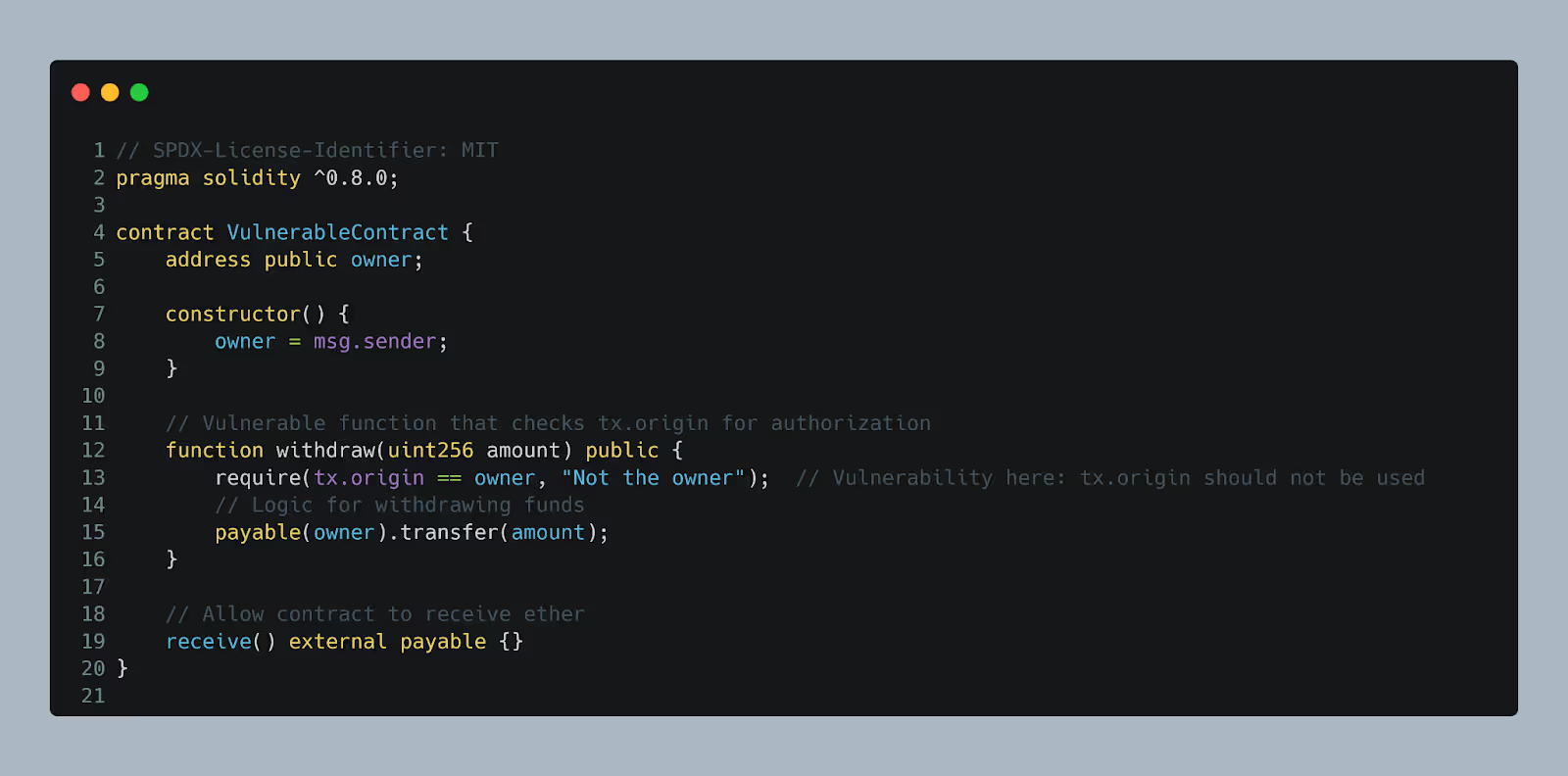
The contract uses tx.origin to check ownership, which is dangerous because if the contract is called by another contract (rather than directly by the owner), it incorrectly grants permissions to the attacker using a contract intermediary.
How to Mitigate:
- Always double-check URLs and only use verified, official websites.
- Never share your private key, seed phrase, or wallet credentials with anyone.
- Use hardware wallets to store funds securely and keep keys offline.
Best Practices for Mitigating Web3 Security Vulnerabilities
To address the security vulnerabilities in Web3, here are a few best practices:
- Conduct Thorough Audits: Always audit smart contracts and decentralized applications (dApps) before deployment. Regular audits help identify vulnerabilities that might otherwise go unnoticed.
- Educate Users: User awareness is one of the best ways to combat phishing and social engineering attacks. Promote best practices such as using hardware wallets and being cautious of unsolicited offers.
- Implement Multi-Signature Protocols: For high-value transactions or funds, multi-signature protocols add an additional layer of security by requiring multiple approvals before a transaction can be completed.
- Stay Up-to-Date: Keep your software, protocols, and security libraries up-to-date to protect against known vulnerabilities.
- Test and Monitor: Continuously monitor for suspicious activity, perform penetration testing, and have a rapid response plan in place in case of a breach.
Conclusion
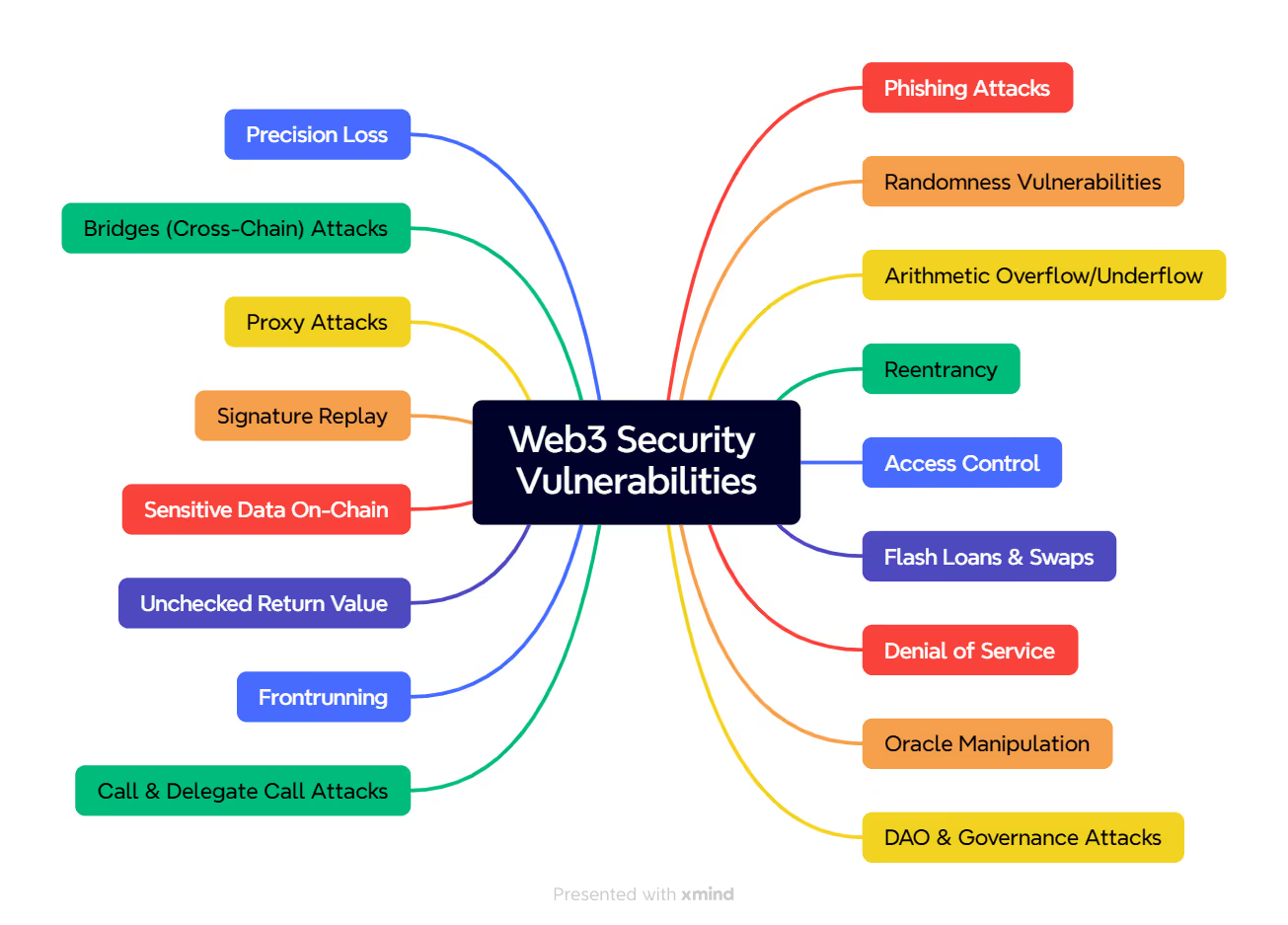
Web3 technologies offer incredible potential, but they also introduce unique security challenges. From smart contract vulnerabilities and phishing attacks to issues with tokenomics and cross-chain bridges, Web3 security requires constant vigilance. By understanding these vulnerabilities and following best practices, we can help make the decentralized web a safer space for all users. Below is a chart representing the distribution of these common Web3 vulnerabilities to help visualize the most frequently encountered issues in the space.





.avif)

