Pentesting vs. Ethical Hacking: What is the difference?
In the field of cybersecurity, understanding the difference between penetration testing (pentesting) and ethical hacking is essential for building a comprehensive defense strategy. Both aim to uncover vulnerabilities within systems and networks, but they differ significantly in approach, methodology, and scope. Pentesting follows a structured methodology to identify specific weaknesses, while ethical hacking takes a broader, often more adaptive, approach that mirrors real-world attack scenarios.
For cybersecurity teams tasked with protecting complex infrastructures, understanding these differences can optimize resources and enhance response strategies. Let’s explore how these approaches differ, where each adds value, and why both are critical.
What is pentesting?
Pentesting is a systematic approach to evaluating the security of a system, network, or application. The goal is to identify potential vulnerabilities before they can be exploited by real attackers. Pentesters simulate cyberattacks, following a defined scope and methodology to determine weaknesses that need attention.
Key characteristics of pentesting:
- Structured and Methodical: Pentesters follow a predefined scope, such as testing specific applications or network components.
- Project-Based: Pentests are often performed as one-time assessments, helping organizations to evaluate security at specific intervals.
- Detailed Reporting: Pentesters provide a report that details vulnerabilities, risk levels, and potential impact, offering actionable recommendations for fixing issues.
Popular pentesting frameworks:
- OWASP (Open Web Application Security Project): Focused on web application security.
- NIST 800-115: A US standard that outlines guidelines for information security testing.
- OSSTMM (Open Source Security Testing Methodology Manual): Provides a rigorous framework for testing security across various systems.
What is ethical hacking?
Ethical hacking encompasses a broader range of activities. Ethical hackers are often granted more freedom to assess any vulnerabilities within a system. Their role isn’t limited to a specific scope, allowing them to think and act like real-world attackers.
Key characteristics of ethical hacking:
- Comprehensive Approach: Ethical hackers often test an organization’s security defenses from multiple angles, including social engineering and phishing attacks.
- Continuous Engagement: Ethical hacking may be ongoing, with hackers constantly assessing systems for weaknesses as part of a security team.
- Creative Problem Solving: Ethical hackers have the flexibility to find unconventional vulnerabilities, exploring beyond predefined boundaries to ensure comprehensive security.
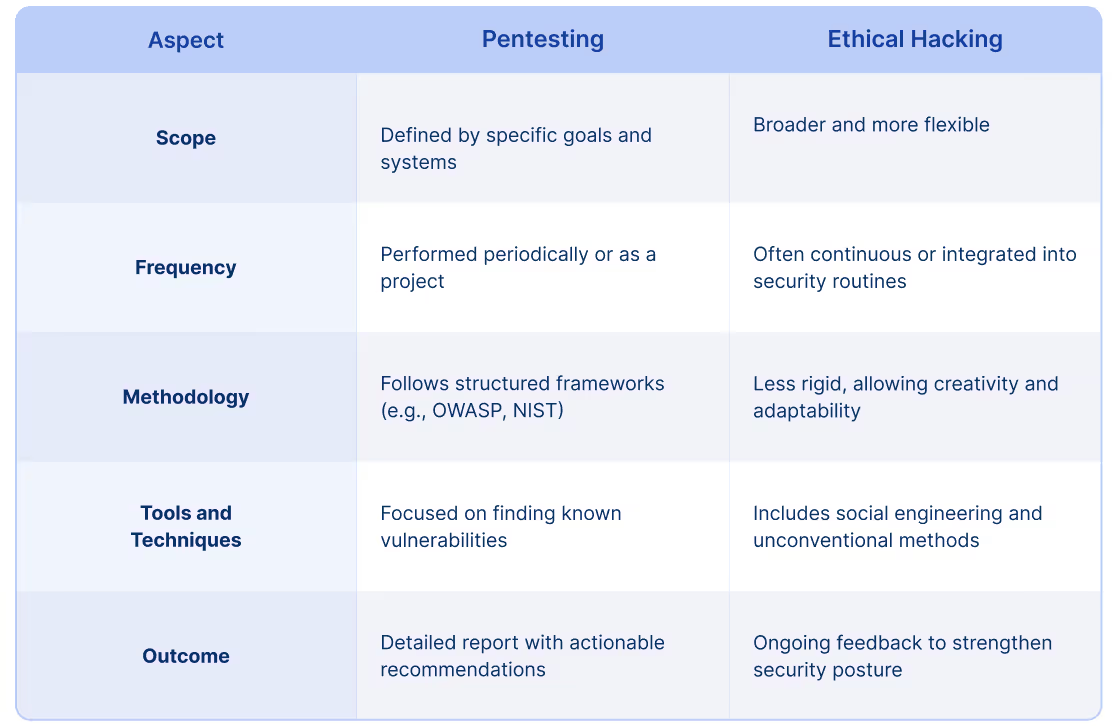
Core differences between pentesting and ethical hacking
While both pentesters and ethical hackers aim to find security weaknesses, here’s a closer look at the distinctions:
Which approach is right for your business?
Choosing between pentesting and ethical hacking depends on your organization’s needs:
Pentesting is ideal for businesses seeking to validate the security of specific applications or networks. It’s useful for compliance and regulatory checks and can be scheduled periodically to ensure continued security.
Ethical hacking suits organizations looking for a continuous and proactive security approach. It’s particularly valuable for companies handling sensitive data who want consistent monitoring and rapid responses to new threats.
Whether pentesting or ethical hacking is the best fit, cybersecurity measures must be tailored to an organization’s risk profile, regulatory requirements, and budget. Strike, for instance, offers solutions that integrate both structured pentesting and innovative, ethical hacking approaches to provide businesses with comprehensive protection against cyber threats.






.avif)