Running workflows with Task Ninja

Many cybersecurity professionals, especially those engaged in offensive exercises such as "Ethical Hacking" in consultancy services or "Bug Bounty" contexts, often have something in common: They standardize a significant portion of their workflow. In other words, they use a "methodology," which will be the guide throughout the different stages of the ongoing exercises.
Methodology: What do we mean?
When we refer to "methodologies," we should think of them as mechanisms that aim to standardize a workflow through an ordered set of procedures, ultimately guiding the task of attacking or solving a common problem.
Methodologies are developed based on professional experience, and due to their nature, they are not rigid as they tend to change as much as the experience of those who develop and execute them. These changes will always be in favor of achieving improvements in execution times and the results obtained.
Entering the context of cybersecurity, where, for example, evaluating the security of a web application is necessary, the role of the applied methodology will be to determine the steps to align in searching, identifying, cleaning, and organizing the obtained results. Finally, it involves analyzing potential security issues that will likely end up being documented in a report.
Additionally, it is worth mentioning that a good methodology is one that can adapt to last-minute changes such as:
- Project scope.
- Infrastructure changes.
- During the evaluation stage, e.g., a new functionality, module, or web component.
- Service outages or blocks.
- And many other factors that depend on the context of each project.
Workflows with Task Ninja
If our readers have reached this point in the article, they probably already have a general idea of what a methodology is, what it represents, and its contribution. If that's the case, I'm here to introduce a tool that collaborates in a friendly way with the development of a methodology for any cybersecurity professional.
I'm referring to the utility called Task Ninja, which, according to the definition found in the project repository, is a versatile and extensible task automation framework designed to simplify and optimize your workflow. Whether you're managing complex tasks, automating routine operations, or orchestrating a series of commands.
The project repository mentioned is the following: https://github.com/RikunjSindhwad/Task-Ninja
Task Ninja requires the loading of a YAML file through an argument (-workflow) to function. The described tasks will be executed within containers (Docker). The executed tasks will have the ability to take results from one container and pass them to the next by simply specifying the input in the YAML.
In summary, this file defines the tasks to be executed, how they will be performed, in what order, and how the output of the tools will be processed.
The structure of the YAML is very simple and is divided into three parts: (config), (vars), (tasks).
- Configuration: Here, all possible global configurations for the workflow can be defined.
- Vars: Vars contain variables that can be reused in the workflow. It acts as a placeholder for keys {{}} that contain variable names defined in the command, inputs, and dynamic files that are part of the task structure.
- Tasks: Tasks contain the configuration of different tasks and their command with some additional features it offers.
In practice, a YAML file looks like this:
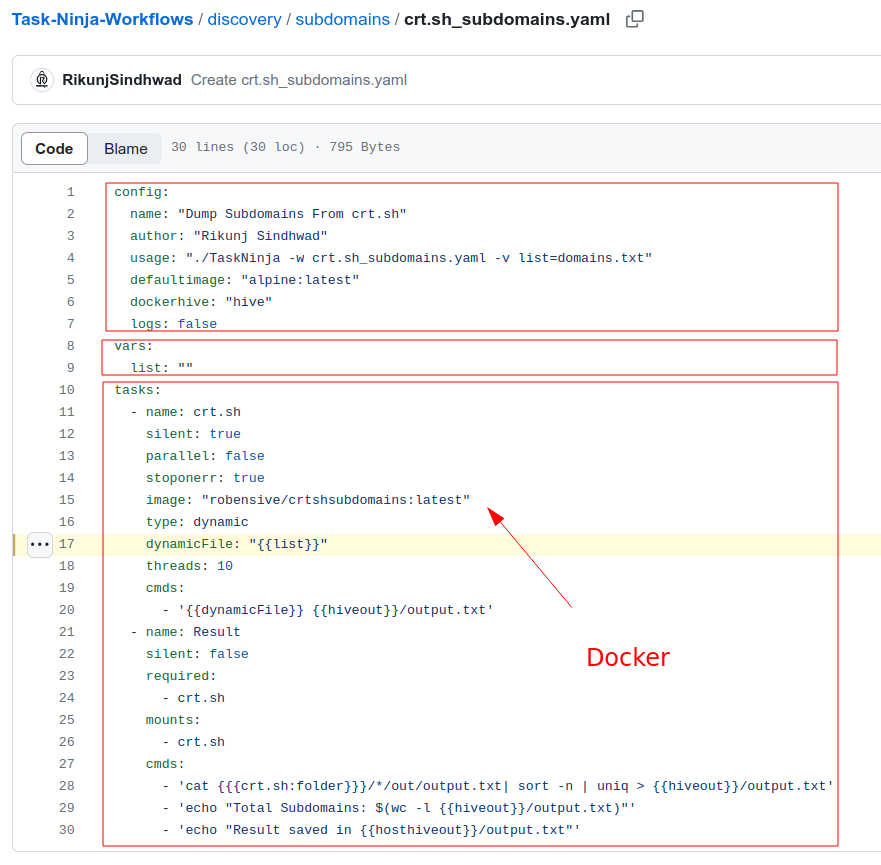
Manipulating or creating one of these files does not involve any special technical complexity. It is valid to state that its structure, besides being user-friendly, is sufficiently documented to address any doubts that may arise regarding specific configurations one wishes to achieve.
Documentation and Project Sources:
- https://github.com/RikunjSindhwad/Task-Ninja/wiki/TaskNinja-Wiki-(v2)
- https://github.com/RikunjSindhwad/Task-Ninja
- https://github.com/RikunjSindhwad/Task-Ninja-Workflows/
- https://www.youtube.com/watch?v=Kjvv0LRHWy8
- https://www.youtube.com/watch?v=3N7C2rNoITU
Getting Started with TaskNinja
Pre-Requirements Check:
Before starting with TaskNinja, ensure that the following prerequisites are met:
- Docker Installation
- Golang Installation
Option 1:
To get started with TaskNinja, follow these steps:
- Installation: Learn how to install Task Ninja on your system.
git clone https://github.com/RikunjSindhwad/Task-Ninja.git cd Task-Ninja go build ./Robensive-TaskNinja
Option 2:
GO111MODULE=on go install github.com/RikunjSindhwad/Task-Ninja@latest
- Validate that it is installed correctly:
Task-Ninja --help
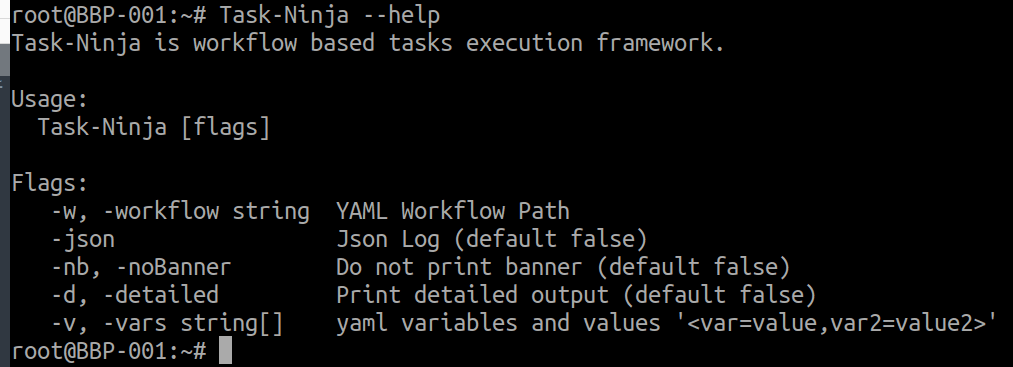
- There are NO more steps, it's that easy :)
Usage Example
There is a second repository within the same project that contains fully functional workflows. You can find it here: https://github.com/RikunjSindhwad/Task-Ninja-Workflows
The official YAML files that are available for use are as follows:
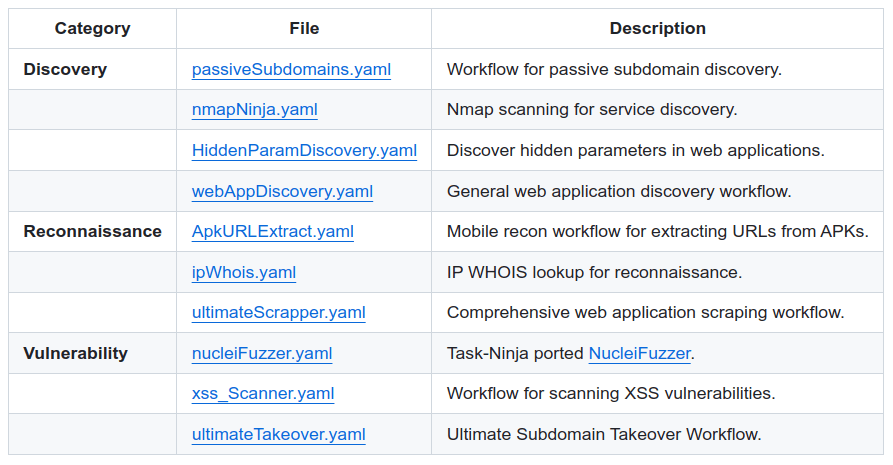
For the proof of concept of using TaskNinja, I will make use of the workflow) prepared for passive subdomain reconnaissance.
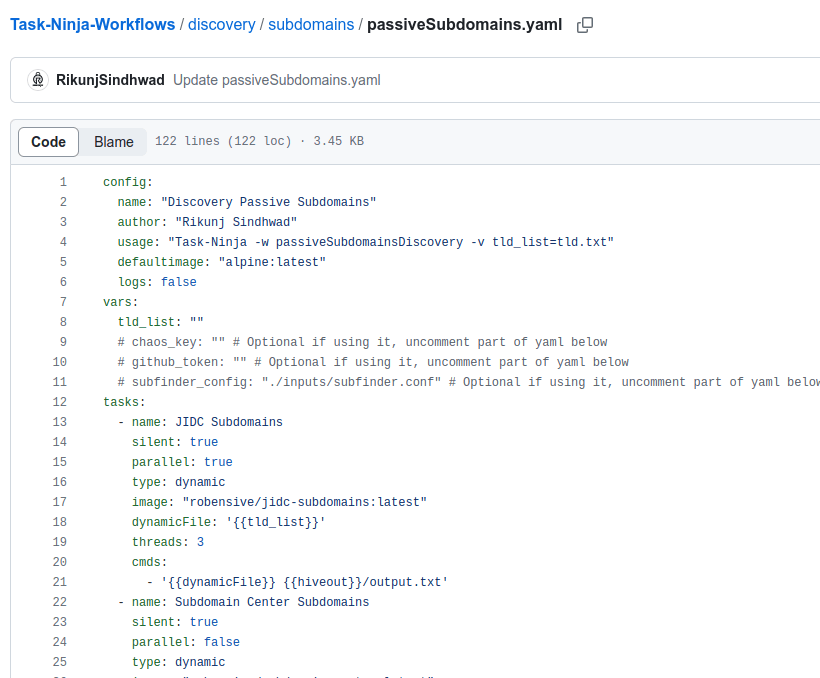
The selected domain for the proof of concept is: 'starbucks.com'.
Clarification regarding the program used in this mini POC: "Starbucks" has a public bug bounty program (https://hackerone.com/starbucks), which enables us to conduct these types of tests.
Execution:
Task-Ninja -w ninja/Task-Ninja-Workflows/discovery/subdomains/passiveSubdomains.yaml -nb -v tld_list=domain_target.txt
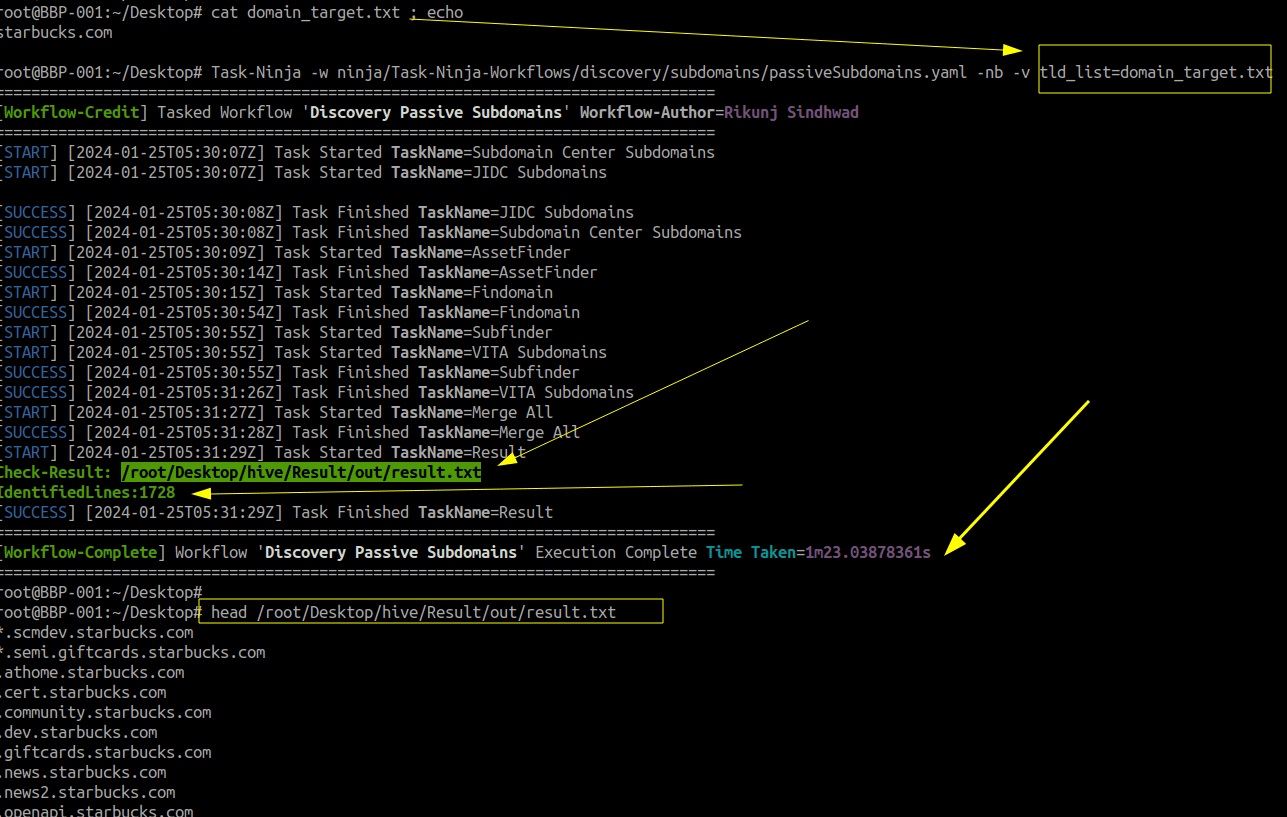
Regarding the output of the tool, it can be summarized as having the right and necessary details:
- Task name in progress
- Start and end time of each task
- Location of the resource where the final result, processed by the assigned tasks, is stored
- Number of lines obtained from the final file
- Total time consumed from the execution of the utilized YAML until completion
Final Thoughts
If you are professionally involved in cybersecurity and are interested in automating your methodology or a part of it, I strongly recommend giving this utility a chance to handle the repetitive tasks that are part of any offensive security exercise.
And if, in the end, "TaskNinja" meets your expectations, I encourage you to make improvements to the current YAML files and, why not, develop new YAML files that you might consider sharing with the community.






.avif)