This is why businesses without a vulnerability manager are at risk
Cybersecurity threats are no longer limited to large corporations or specific industries—they target businesses of all sizes. Yet, many organizations continue to overlook one of the most effective ways to minimize risk: hiring or designating a vulnerability manager. This role goes beyond simply identifying potential weaknesses; it creates a structured approach to managing and mitigating vulnerabilities across the organization.
If your company operates without someone dedicated to this function, the risks can be significant. Let’s dive into why this role is critical and how it can transform your cybersecurity strategy.
Unmanaged vulnerabilities: A ticking time bomb
Every software application, system, and device connected to your network represents a potential entry point for attackers. Vulnerabilities—whether caused by outdated software, misconfigurations, or unpatched systems—are often the easiest targets.
Without a vulnerability manager, businesses risk falling behind on security updates, leaving them exposed to increasingly sophisticated cyberattacks. Studies show that most breaches exploit known vulnerabilities that could have been addressed. Without a clear owner of this responsibility, it’s easy for these critical tasks to fall by the wayside, creating long-term risks that grow over time.
Beyond identification: The true value of a vulnerability manager
The role of a vulnerability manager goes far beyond identifying issues. It’s about building a system of accountability and prioritization. In many organizations, vulnerabilities are identified but not addressed promptly due to competing priorities or a lack of coordination across teams.
A vulnerability manager serves as the linchpin, ensuring that:
- Vulnerabilities are assessed based on risk and business impact.
- Patches and updates are deployed in a timely manner.
- Security gaps are communicated to decision-makers for informed action.
Their role also involves ensuring compliance with regulations and industry standards, which can help avoid penalties and legal repercussions. Without this role, the gaps in your vulnerability management process could remain unnoticed until it’s too late.
Vulnerability management is a team effort
While the vulnerability manager plays a key role, they don’t operate in isolation. Effective vulnerability management requires collaboration across departments, including IT, DevOps, and compliance teams. Without a dedicated manager to oversee this effort, communication gaps can lead to delays, misaligned priorities, or worse—ignored vulnerabilities.
By centralizing responsibility under a vulnerability manager, businesses create a cohesive strategy that bridges technical and operational goals. This ensures vulnerabilities are addressed promptly and efficiently, reducing the risk of exploitation.
How Strike’s Vulnerability Manager simplifies security
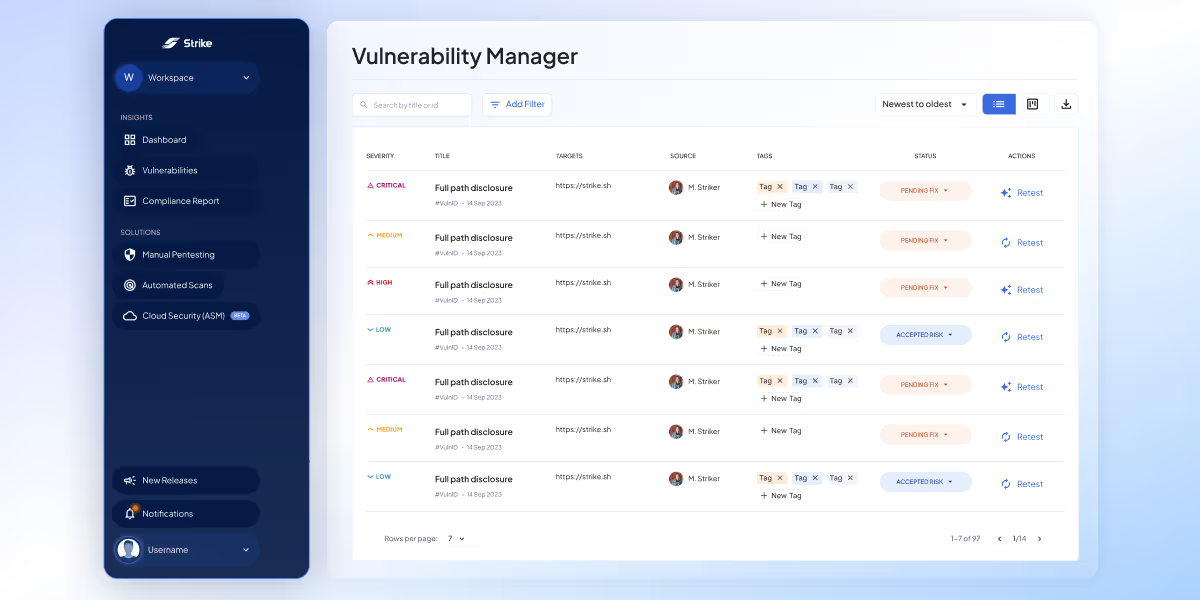
Strike enhances pentesting efforts with advanced technology, providing a centralized view of vulnerabilities in one place.
The Vulnerability Manager links each vulnerability to a specific target, detailing the exact URL where it was identified and the source of the discovery. For findings from a pentest, the name of the pentester is included, while vulnerabilities detected through automated scans include comprehensive details as well.
Key features include:
- A Status property (Retest request, In progress, Accepted Risk, Solved, False Positive), allowing vulnerabilities to be moved between statuses to streamline organization and collaboration within teams.
- Integration with external tools, such as Jira, for seamless workflow management.
- Filters -including Severity, Source, and Tags- and a search bar to quickly locate specific vulnerabilities.
- A kanban view, accessible in the top right corner, for intuitive project management.
- A Retest option directly within the platform to simplify follow-up actions.
For a broader perspective, the Dashboard offers an at-a-glance analysis of the overall security posture.
Strike’s Vulnerability Manager makes managing vulnerabilities intuitive and effective. To learn more, explore the platform or schedule a demo with the technical team.